DES加密算法【Java实现】 |
您所在的位置:网站首页 › 密文和明文等长文的区别 › DES加密算法【Java实现】 |
DES加密算法【Java实现】
|
文章目录
简单介绍算法流程IP置换子密钥 Ki 的获取密码函数 f逆IP置换其他
代码实现总结和思考参考文献
简单介绍
DES算法为密码体制中的对称密码体制,又被称为美国数据加密标准,2000年以前一直是业界的标准。DES是一个分组加密算法,以64位为分组对数据加密(每次处理固定长度的数据段,称之为分组)。如果加密的数据长度不是64位的倍数,可以按照某种具体的规则来填充位。DES的明文长为64位,密钥长64位,但密钥事实上是56位参与DES运算(第8、16、24、32、40、48、56、64位是校验位,使得每个密钥都有奇数个1),分组后的明文组和56位的密钥按位替代或交换的方法形成密文组。DES算法具体通过对明文进行一系列的排列和替换操作来将其加密。DES 解密算法与加密算法完全相同,只需要将子密钥的使用顺序反过来就行了。
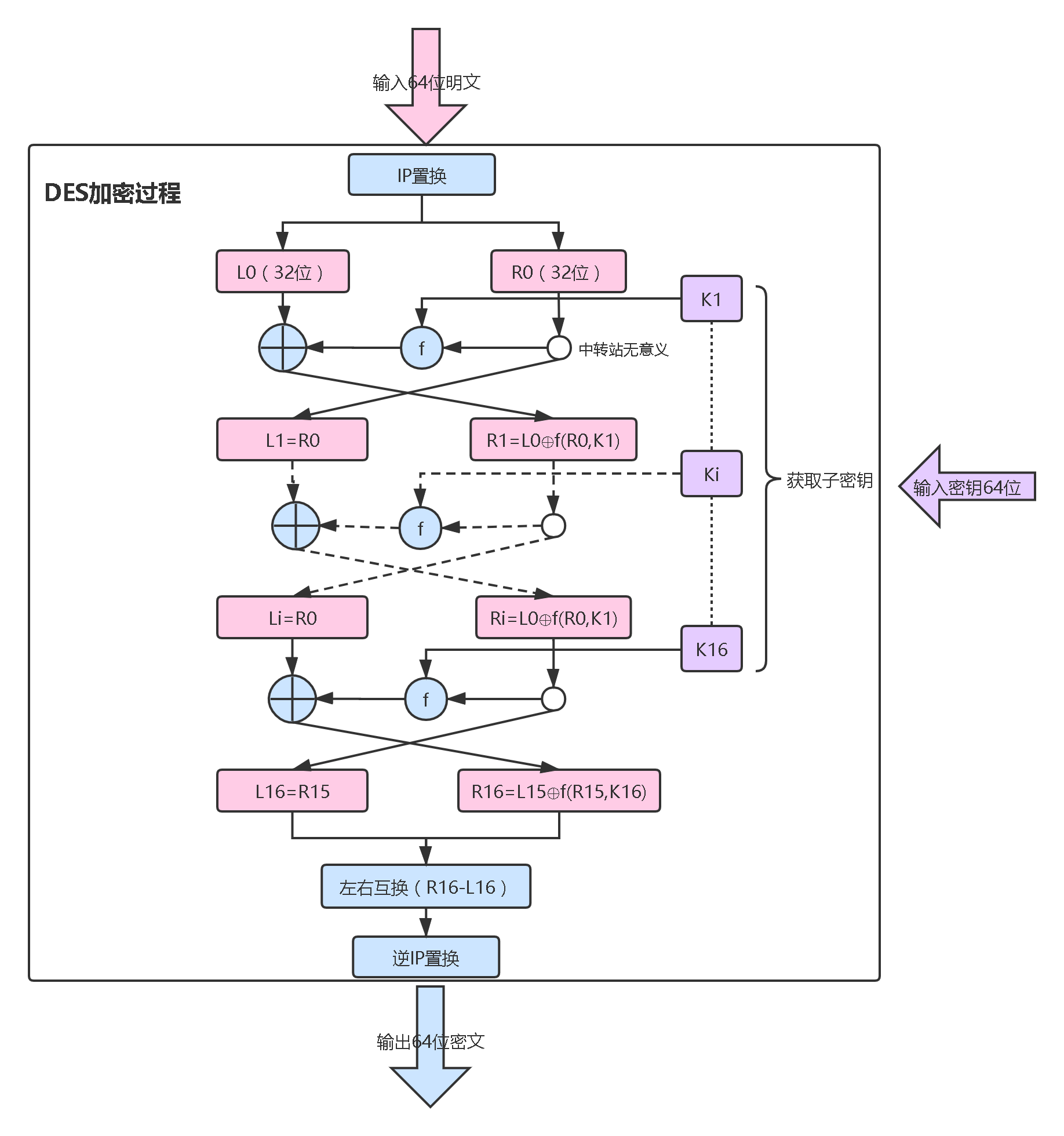
算法流程
DES加密算法流程总体如上图所示,主体内容为中间操作(包括密码函数f和异或操作)循环16次。 DES加密算法五个最值得注意的部分为: IP置换;子密钥 Ki 的获取;密码函数 f ;逆IP置换;其他; IP置换IP(initial permutation 初始排列)是一个 8x8 的置换表: // Replacement Table(RT) final int RT_IP[] = { 58, 50, 42, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4, 62, 54, 46, 38, 30, 22, 14, 6, 64, 56, 48, 40, 32, 24, 16, 8, 57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3, 61, 53, 45, 37, 29, 21, 13, 5, 63, 55, 47, 39, 31, 23, 15, 7 };IP置换表的含义为:原来的58位现在排在第一位,50位排在第二位…以此类推【下文所有置换都是这个含义】。注:该过程输入是64位的分组,IP置换以后得到的是一个 64 位的输出。 子密钥 Ki 的获取
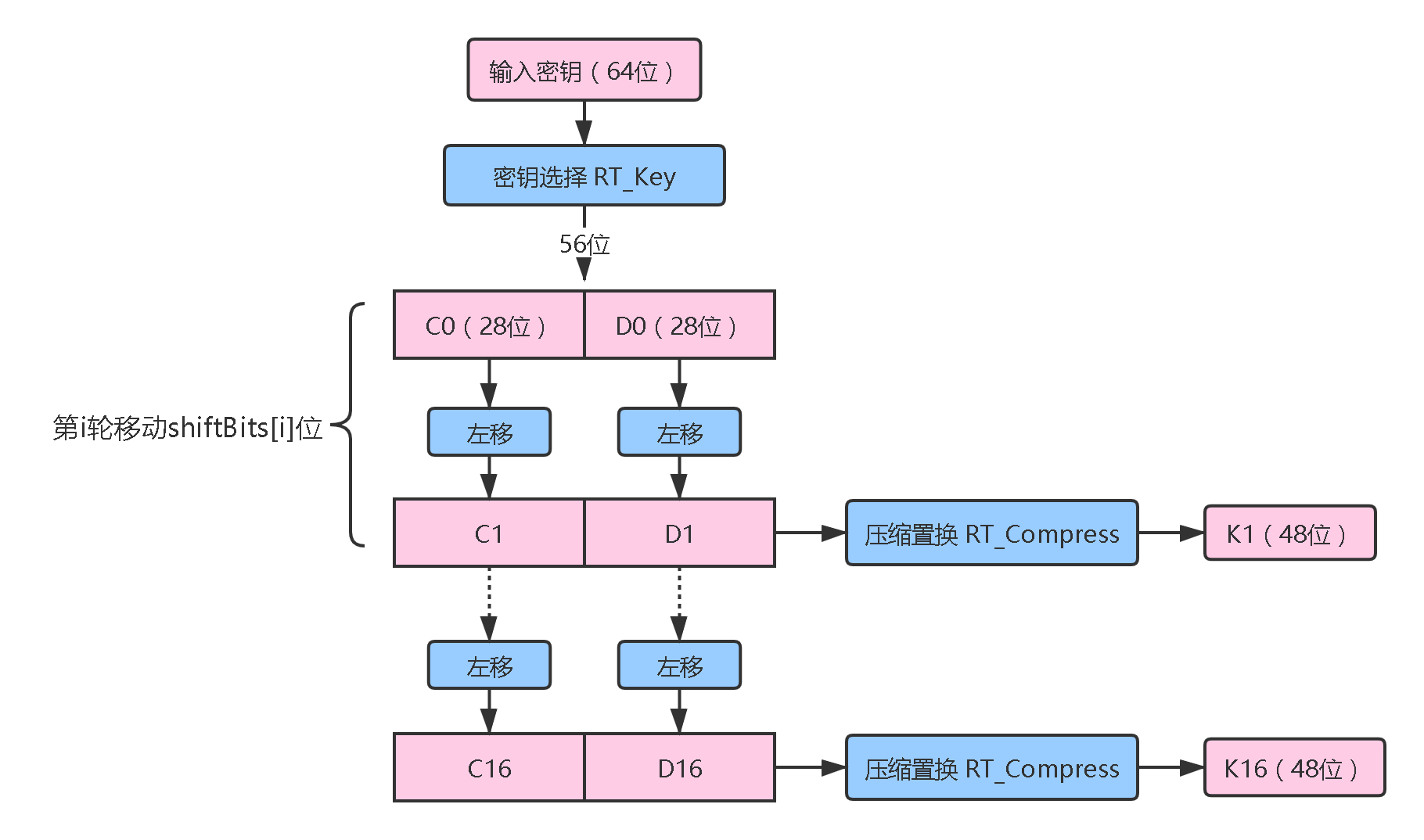
根据密钥选择置换表RT_Key,将 64 位输入密钥变成 56 位。(去掉了奇偶校验位) 将RT_Key置换得到的 56 位密钥(其实这也是一种压缩置换,特指去掉了奇偶校验位的过程),分为前28位 C0 和后28位 D0,分别对它们进行循环左移,C0左移得到 C1,D0 左移得到 D1。 将 C1 和 D1 合并,然后通过RT_Compress表进行压缩置换,得到当前这一轮的 48 位子密钥 K1 。 然后对 C1 和 D1 进行左移和压缩置换,获取下一轮的子密钥……一共进行16轮,得到 16 个 48 位的子密钥。 这部分需要用到的置换表和移动位数记录等常量如下: // 密钥选择(置换)表,64位密钥去掉校验位,选择剩下的56位作为新的密钥。可以发现,去掉校验位的同时还打乱了顺序 final int RT_Key[] = {57, 49, 41, 33, 25, 17, 9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35, 27, 19, 11, 3, 60, 52, 44, 36, 63, 55, 47, 39, 31, 23, 15, 7, 62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21, 13, 5, 28, 20, 12, 4}; // 压缩置换表,将56位密钥压缩成48位子密钥,同时打乱顺序 final int RT_Compress[] = {14, 17, 11, 24, 1, 5, 3, 28, 15, 6, 21, 10, 23, 19, 12, 4, 26, 8, 16, 7, 27, 20, 13, 2, 41, 52, 31, 37, 47, 55, 30, 40, 51, 45, 33, 48, 44, 49, 39, 56, 34, 53, 46, 42, 50, 36, 29, 32}; // 每轮左移的位数 final int shiftBits[] = {1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1}; 密码函数 f
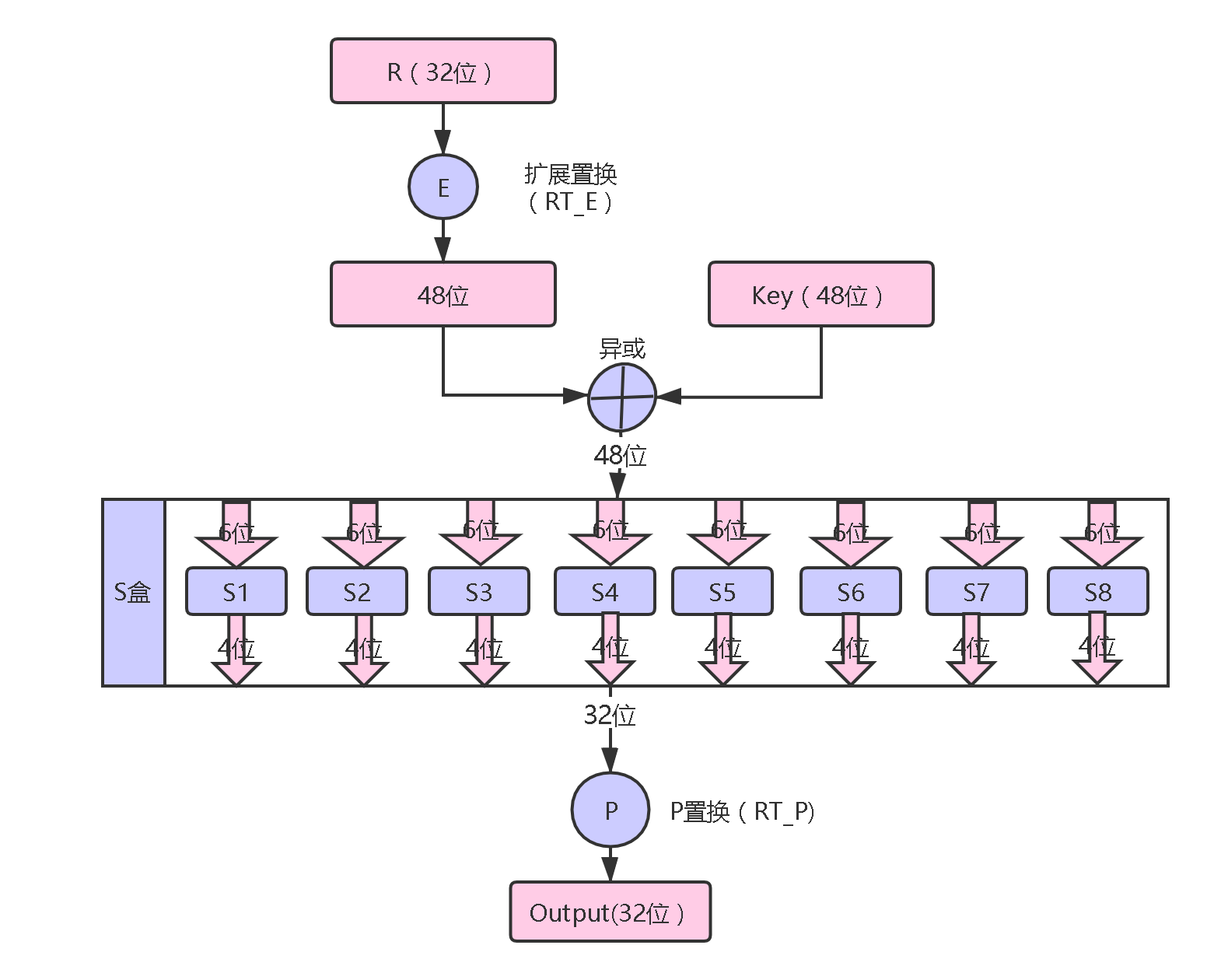
密码函数f(R, K)接受两个输入:32 位的R数据(明文的右半部分)和 48 位的子密钥(Ki)。然后: 通过表 E 进行扩展置换,将输入的 32 位数据扩展为 48 位; 将扩展后的 48 位数据与 48 位的子密钥进行异或运算; 将异或得到的 48 位数据分成 8 个 6 位的块,每一个块通过对应的一个 S 表产生一个 4 位的输出。其中,每个 S 表都是 4 行 16 列。具体的置换过程如下:把 6 位输入中的第 1 位和第 6 位取出来行成一个两位的二进制数 x ,作为 Si 表中的行数(0~3);把 6 位输入的中间 4 位构成另外一个二进制数 y,作为 Si 表的列数(0~15);查出 Si 表中 x 行 y 列所对应的整数,将该整数转换为一个 4 位的二进制数。 把通过 S 表置换得到的 8 个 4 位连在一起,形成一个 32 位的数据。然后将该 32 位数据通过表 P 进行置换(称为P-置换),置换后得到一个仍然是 32 位的结果数据,这就是f(R, K)函数的输出。 这部分用到了扩展置换表RT_E,8个S表以及P-置换表(RT_P),如下: // 扩展置换表 RT_E,将32位扩展至48位 final int RT_E[] = {32, 1, 2, 3, 4, 5, 4, 5, 6, 7, 8, 9, 8, 9, 10, 11, 12, 13, 12, 13, 14, 15, 16, 17, 16, 17, 18, 19, 20, 21, 20, 21, 22, 23, 24, 25, 24, 25, 26, 27, 28, 29, 28, 29, 30, 31, 32, 1}; // S盒,每个S盒Si是4x16的置换表,6位 -> 4位 final int S_BOX[][][] ={ { {14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7}, {0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8}, {4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0}, {15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13} }, { {15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10}, {3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5}, {0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15}, {13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9} }, { {10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8}, {13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1}, {13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7}, {1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12} }, { {7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15}, {13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9}, {10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4}, {3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14} }, { {2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9}, {14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6}, {4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14}, {11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3} }, { {12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11}, {10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8}, {9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6}, {4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13} }, { {4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1}, {13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6}, {1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2}, {6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12} }, { {13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7}, {1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2}, {7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8}, {2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11} } }; // P置换,32位 -> 32位 final int RT_P[] = {16, 7, 20, 21, 29, 12, 28, 17, 1, 15, 23, 26, 5, 18, 31, 10, 2, 8, 24, 14, 32, 27, 3, 9, 19, 13, 30, 6, 22, 11, 4, 25 }; 逆IP置换合并 L16 和 R16 得到一个 64 位的数据,再经过尾置换后得到的就是 64 位的密文。注意:要将 L16和 R16 合并成 R16L16(即左右互换)。逆IP置换表如下: // 逆IP置换表 final int RT_InverseIP [] = {40, 8, 48, 16, 56, 24, 64, 32, 39, 7, 47, 15, 55, 23, 63, 31, 38, 6, 46, 14, 54, 22, 62, 30, 37, 5, 45, 13, 53, 21, 61, 29, 36, 4, 44, 12, 52, 20, 60, 28, 35, 3, 43, 11, 51, 19, 59, 27, 34, 2, 42, 10, 50, 18, 58, 26, 33, 1, 41, 9, 49, 17, 57, 25};注意:逆IP置换就是IP置换的反操作,A经过IP置换得到B,那B经过逆IP置换就可以得到A。逆IP置换表中第一个数是40,而IP置换表中,第40个元素为1。 现在我们可以回到本文的开头,去看看 DES 算法的整体流程图,思路就已经很清楚了。 其他 异或运算(图中的⊕符号)是指两个多位比特流之间的异或,操作为:对比特流逐位采用异或运算再拼接起来。异或运算规则为:[相同为0,不同为1,即1 ^ 1 = 0;0 ^ 0 = 0;1 ^ 0 = 1] 代码实现 package lesson; public class DES { // Replacement Table(RT)IP置换表 final static int[] RT_IP = { 58, 50, 42, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4, 62, 54, 46, 38, 30, 22, 14, 6, 64, 56, 48, 40, 32, 24, 16, 8, 57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3, 61, 53, 45, 37, 29, 21, 13, 5, 63, 55, 47, 39, 31, 23, 15, 7 }; // 密钥选择(置换)表,64位密钥去掉校验位,选择剩下的56位作为新的密钥。可以发现,去掉校验位的同时还打乱了顺序 final static int[] RT_Key = {57, 49, 41, 33, 25, 17, 9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35, 27, 19, 11, 3, 60, 52, 44, 36, 63, 55, 47, 39, 31, 23, 15, 7, 62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21, 13, 5, 28, 20, 12, 4}; // 压缩置换,将56位密钥压缩成48位子密钥 final static int[] RT_Compress = {14, 17, 11, 24, 1, 5, 3, 28, 15, 6, 21, 10, 23, 19, 12, 4, 26, 8, 16, 7, 27, 20, 13, 2, 41, 52, 31, 37, 47, 55, 30, 40, 51, 45, 33, 48, 44, 49, 39, 56, 34, 53, 46, 42, 50, 36, 29, 32}; // 每轮左移的位数 final static int[] shiftBits = {1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1}; // 扩展置换表 RT_E,将32位扩展至48位 final static int[] RT_E = {32, 1, 2, 3, 4, 5, 4, 5, 6, 7, 8, 9, 8, 9, 10, 11, 12, 13, 12, 13, 14, 15, 16, 17, 16, 17, 18, 19, 20, 21, 20, 21, 22, 23, 24, 25, 24, 25, 26, 27, 28, 29, 28, 29, 30, 31, 32, 1}; // S盒,每个S盒Si是4x16的置换表,6位 -> 4位 final static int[][][] S_BOX ={ { {14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7}, {0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8}, {4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0}, {15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13} }, { {15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10}, {3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5}, {0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15}, {13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9} }, { {10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8}, {13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1}, {13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7}, {1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12} }, { {7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15}, {13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9}, {10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4}, {3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14} }, { {2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9}, {14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6}, {4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14}, {11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3} }, { {12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11}, {10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8}, {9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6}, {4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13} }, { {4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1}, {13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6}, {1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2}, {6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12} }, { {13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7}, {1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2}, {7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8}, {2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11} } }; // P置换,32位 -> 32位 final static int[] RT_P = {16, 7, 20, 21, 29, 12, 28, 17, 1, 15, 23, 26, 5, 18, 31, 10, 2, 8, 24, 14, 32, 27, 3, 9, 19, 13, 30, 6, 22, 11, 4, 25 }; // 逆IP置换表 final static int[] RT_InverseIP = {40, 8, 48, 16, 56, 24, 64, 32, 39, 7, 47, 15, 55, 23, 63, 31, 38, 6, 46, 14, 54, 22, 62, 30, 37, 5, 45, 13, 53, 21, 61, 29, 36, 4, 44, 12, 52, 20, 60, 28, 35, 3, 43, 11, 51, 19, 59, 27, 34, 2, 42, 10, 50, 18, 58, 26, 33, 1, 41, 9, 49, 17, 57, 25}; /**********************************************************************/ /* */ /* 下面是DES算法实现 */ /* */ /**********************************************************************/ //生成16个子密钥 public static StringBuffer[] GenerateSubKey(StringBuffer str, boolean flag) throws Exception{ if(str.length()!=64){ throw new Exception("输入密钥长度不是64位!"); } else { //密钥选择 StringBuffer choosedKey = new StringBuffer(); for (int i = 0; i < RT_Key.length; i++) { choosedKey.append(str.charAt(RT_Key[i]-1)); } //拆分密钥 // System.out.println("choosedKey.length():"+choosedKey.length()); StringBuffer leftString = new StringBuffer(choosedKey.substring(0,28)); StringBuffer rightString = new StringBuffer(choosedKey.substring(28,56)); //16次循环得到16个子密钥 StringBuffer[] res = new StringBuffer[16]; for (int i = 0; i < 16; i++) { int shiftBit=shiftBits[i]; //两部分密钥分别左移 StringBuffer temp_left=new StringBuffer(leftString); StringBuffer temp_right=new StringBuffer(rightString); for (int j = 0; j < leftString.length(); j++) { if(j-shiftBit |
【本文地址】
今日新闻 |
推荐新闻 |