两款实用的DDos攻击工具 |
您所在的位置:网站首页 › cc测压工具 › 两款实用的DDos攻击工具 |
两款实用的DDos攻击工具
|
两款实用的DDos攻击工具
2018-02-22Network • Security865 之前为了重现某个bug,需要对网络设备进行ddos攻击测试,同时也是对设备的网络攻击防护功能进行抗压测试。临阵磨枪,google了两款攻击工具,windows平台的hyenae,以及Linux平台的hping3,在此记录一下两者的用法。 Hyenaehyenae是在Windows平台上非常好用的一款ddos攻击工具,可以完成绝大多数的攻击操作。 download https://sourceforge.net/projects/hyenae/ Features ARP-Request floodingARP-Cache poisoningPPPoE session initiation floodingBlind PPPoE session terminationICMP-Echo floodingICMP-Smurf attackICMP based TCP-Connection resetTCP-SYN floodingTCP-Land attackBlind TCP-Connection resetUDP floodingDNS-Query floodingDHCP-Discover floodingDHCP starvation attackDHCP-Release forcingCisco HSRP active router hijackingPattern based packet address configurationIntelligent address and address protocol detectionSmart wildcard-based randomizationDaemon for setting up remote attack networks - HyenaeFE QT-Frontend support interface
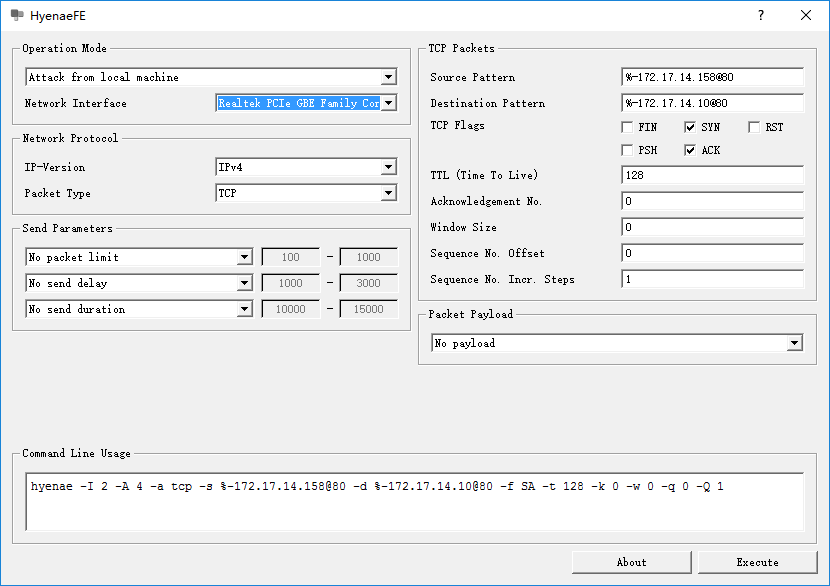
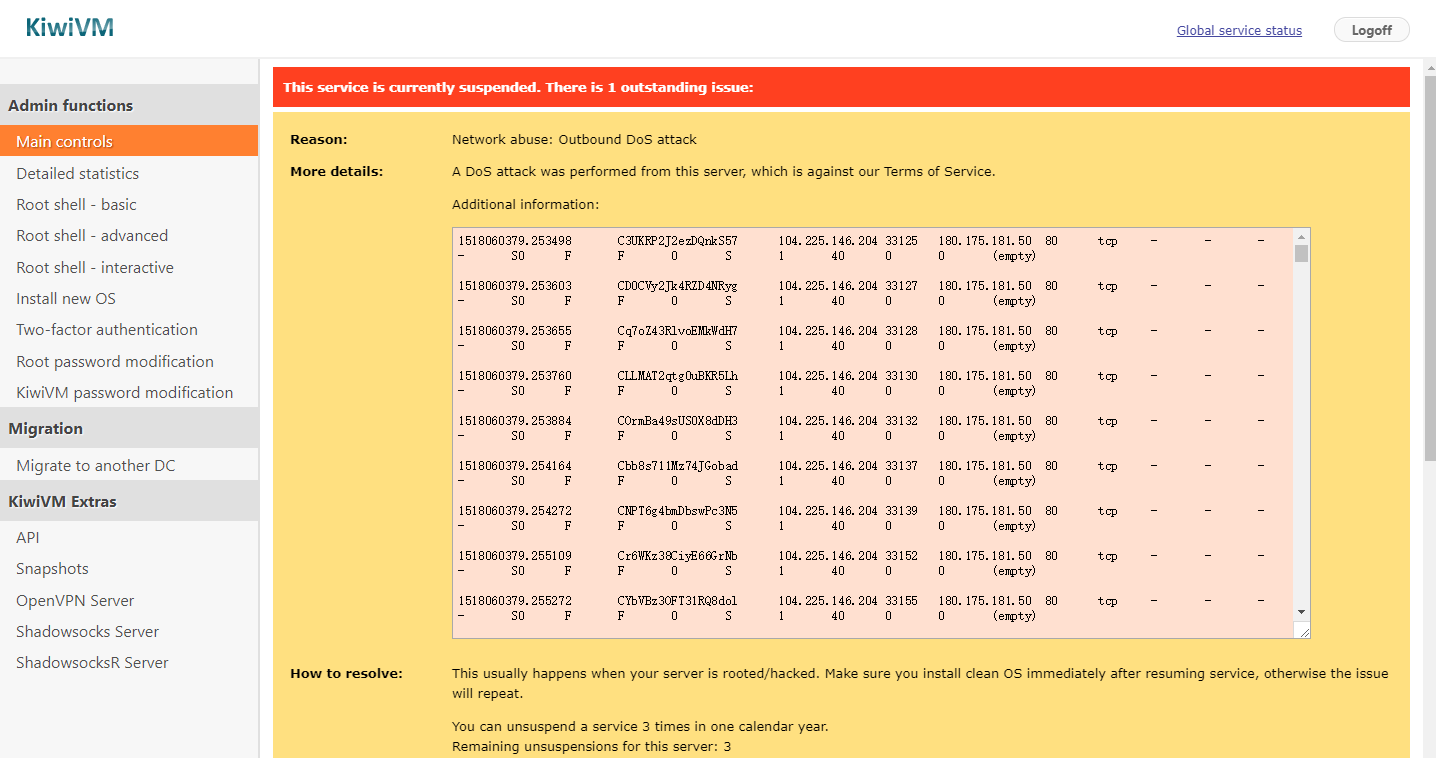
hyenae的界面比较简单,图中展示的是SYN/ACK洪泛攻击的配置选项。 operation mode中可以选择网卡 Network Protocol中可以选择攻击方式对应的网络协议,如SYN洪泛攻击对应传输层的TCP,IP协议可选IPv4, IPv6 攻击源的IP,MAC地址以及端口号可以非常灵活的设置,按MAC-IP@port的格式书写,如图中的攻击源匹配模式%-172.17.14.158@80 % 代表任意,在此处代表任意的MAC地址172.17.14.158为伪造的攻击源IP,可以修改为任意的合法IP80为端口号,80同时也是网络服务器的默认端口 攻击目标的设置方式与攻击源一致,图中的%-172.17.14.10@80 % 随机生成MAC地址172.17.14.10代表被攻击的IP80为攻击目标的被攻击端口号 针对TCP协议,右侧给出其对应的5个常见flags: FIN, SYN, RST, PSH, ACK 可以随意进行单选或多选,以实现不同的攻击方式随意的组合可以产生正常通信过程中无法出现的数据包 软件下方可以设置数据包的发送速率,默认为无限速发送,这会暂用大量带宽,导致网络拥塞;当然啦,这个软件本就是为了攻击网络,导致网络瘫痪正是其目的所在 选择不同的攻击方式,会显示相应不同的配置选项简单说,这幅图的作用是产生MAC地址随机,IP为172.17.14.158,端口为80的伪造源,去攻击目的MAC随机,IP为172.17.14.10的web server。 由于目的MAC随机,当MAC地址首字节为奇数时,生成的数据包为广播包,此时将产生广播风暴,局域网内的所有设备都将收到大量的广播包,当速率很高时,很容易导致局域网瘫痪,这是需要注意的。本人当时年少轻狂,有次测试,使用全速率的广播式SYN/ACK攻击,直接导致部门的局域网瘫痪断网,幸好是晚上,后来找人重置了部门内的网络设备才恢复,想想真是罪过啊。 Use cases Land Attack src: %-172.17.14.94@53des: %-172.17.14.94@80 DoS *** 3118 *** {Land Attack} are suppressed![DoS Attack: Land Attack] from source: 172.17.14.94, port 53,[DoS Attack: Land Attack] from source: 172.17.14.94, port 53,[DoS Attack: Land Attack] from source: 172.17.14.94, port 53, SYN/ACK scan (TCP SYN ACK) src: %-172.17.14.8@80des: %-172.17.14.94@80 DoS *** 3896 *** {SYN/ACK Scan} are suppressed![DoS Attack: SYN/ACK Scan] from source: 172.17.14.8, port 80,[DoS Attack: SYN/ACK Scan] from source: 172.17.14.8, port 80,[DoS Attack: SYN/ACK Scan] from source: 172.17.14.8, port 80, ping flood (icmp echo) src: %-172.17.14.8des: %-172.17.14.94 DoS *** 1881 *** {Ping Flood} are suppressed![DoS Attack: Ping Flood] from source: 172.17.14.8,[DoS Attack: Ping Flood] from source: 172.17.14.8,[DoS Attack: Ping Flood] from source: 172.17.14.8, ping sweep (icmp echo) src: %-%des: %-% DoS *** 1719 *** {Ping Sweep} are suppressed![DoS Attack: Ping Sweep] from source: 188.167.1.1,[DoS Attack: Ping Sweep] from source: 113.172.1.5,[DoS Attack: Ping Sweep] from source: 175.181.2.6, RST Scan(TCP RST) src: %-172.17.14.8@80des: %-172.17.14.94@80 DoS *** 4023 *** {RST Scan} are suppressed![DoS Attack: RST Scan] from source: 172.17.14.8, port 80,[DoS Attack: RST Scan] from source: 172.17.14.8, port 80,[DoS Attack: RST Scan] from source: 172.17.14.8, port 80, ACK scan (TCP ACK) src: %-172.17.14.8@80des: %-172.17.14.94@80 DoS *** 3989 *** {ACK Scan} are suppressed![DoS Attack: ACK Scan] from source: 172.17.14.8, port 80,[DoS Attack: ACK Scan] from source: 172.17.14.8, port 80,[DoS Attack: ACK Scan] from source: 172.17.14.8, port 80 FIN scan(TCP FIN) src: %-172.17.14.8@80des: %-172.17.14.94@80 DoS *** 3009 *** {FIN Scan} are suppressed![DoS Attack: FIN Scan] from source: 172.17.14.8, port 80,[DoS Attack: FIN Scan] from source: 172.17.14.8, port 80,[DoS Attack: FIN Scan] from source: 172.17.14.8, port 80, hping3hping3是用于生成和解析TCPIP协议数据包的开源工具 hping3同样可用于产生ddos攻击包,但与hyenae不同的是,hping3无法手动设置MAC地址,而是根据IP地址自动获取 需要注意的是,如果使用搬瓦工购买的vps向公网IP执行hping3攻击的话,最好不要尝试,如果要用也一定记得限速,否则就会被警告并关停,当然你有3次机会重置
转自: https://www.litreily.top/2018/02/22/ddos-attack/ |
【本文地址】
今日新闻 |
推荐新闻 |