Hacking Wi |
您所在的位置:网站首页 › aircrackguiapk › Hacking Wi |
Hacking Wi
|
Aircrack-ng is a Wi-Fi security auditing tool specifically 802.11 WEP and WPA/WPA2-PSK. It is also used for cracking the WEP and WPA/WPA2-PSK keys for gaining access to a network. Aircrack-ng is used by learning individuals and security professionals to test the security, reliability of wireless networks. It can be installed by using the following command on the terminal: sudo apt-get install aircrack-ngThe attacks range from Wifi Disconnection to obtaining handshakes to cracking passwords. The attacks are to be performed by obtaining the consent of the owner or only on those networks that are owned by you. The first thing that we need to have to successfully attack, audit a network is a Wi-Fi adapter that has monitor mode and allows packet injection. The reason we have to use an external adapter is that the inbuilt adapter that comes along with the PC doesn’t support monitor mode and packet injection. Monitor mode allows the adapter to view and monitor all the traffic received from the wireless network. This mode enables packets to be captured without having to connect or link with an access point.  Cracking WEP
Cracking WEP
WEP(Wired Equivalent Privacy) is a Wi-Fi security protocol, its intention was to provide data confidentiality comparable to that of a traditional wired network. The flaw that we are targeting is Initialisation Vectors(IV), these IVs are 24 bits long. For encryption, Wired Equivalent Privacy (WEP) can use only a 64-bit or 128-bit number, which is made up of a 24-bit Initialization Vector (IV) and a 40-bit or 104-bit default key. The use of short keys reduces the encryption strength because short keys are easy to break, Also it uses an algorithm called RC4 that is deprecated. The Wired Equivalent Privacy (WEP) also creates a detectable pattern for attackers. Each packet is encrypted using a unique key stream.Random initialization vector (IV) is used to generate the keys streams.The initialization vector is only 24 bitsIV + Key (password) = Key stream.The catch here is that the IVs are repeated in a busy network. And this is the vulnerability we are going to use, Repeated IVs can be used to determine the keystream, and ultimately break the encryption. We first need to capture a large number of packets so that we can get enough IVs and store it in a file. The problem here is that if the network is not busy, it would take some time to capture the IVs. We then need to analyze the captured IV and crack the key. To have aircrack-ng conduct a WEP key attack on a capture file, pass it the filename, either in .ivs or .cap/.pcap format. aircrack-ng filename.pcap Cracking WPA/WPA2Wi-Fi Protected Access2- Pre Shared Key is a method of securing one’s network using the option of Pre-Shared key authentication. This kind of mechanism is generally designed for a home environment and not for an enterprise network. The network in this case is encrypted using a plaintext passphrase between 8-63 characters. The passphrase along with the network SSID is used to generate unique encryption keys for each client. Which are constantly changed, thus it is near impossible that the keys are repeated and we can get hold of it. Hacking into a network using WPA/WPA2 protocol is difficult due to the complex algorithm it uses. 
There are two popular methods used to crack WPA/WPA2 WPS methodWPS is a feature that can be used with WPA & WPA2. This allows clients to connect to the network without a password. The authentication is done using an 8 digit pin. This is a vulnerability that exists in routers that ship with this feature enabled by default. Many routers have a specific button dedicated to WPS service. Although this feature can be made redundant by disabling the WPS service using the Configure Router page, unfortunately, most people don’t care about disabling it. 
Generally, WPS forces devices to use an 8-digit numerical PIN system that bypasses the passphrase. As 8 digits pins are comparatively smaller, all the possible combinations can be tried in a shorter time period. This PIN is always checked in groups of two 4-digit codes, and the connecting device is informed whether the four-digit section is correct. Wordlist methodUnlike in the case of WEP, the WPA/WPA2 packet contains no useful data. The only packet that contains data of our interest is the handshake packet. These are 4 packets that are sent to the client to connect to the network. The handshake doesn’t any data that helps to retrieve the key. Rather it helps to verify whether a key is valid or not. We run the following command to intercept the handshake packets. airodump-ng –bssid 00.11.33.22.44.55 –channel 1 –write wpa_handshake mon0This command will write the handshake to the wpa_handshake file. To obtain a handshake we need to disconnect the client so that when the connection is re-established we can intercept it. airplay-ng -0 1 -a B6:14:6C:7E:40:9D -c 00:0F:B5:AE:CE:9D mon0 here 0 means deauthentication and we are sending 1 deauthentication packet here.-a B6:14:6C:7E:40:9D is the MAC address of the access point-c 00:0F:B5:34:30:30 is the MAC address of the client to deauthenticatemon0 is the interface nameFinally, we use the handshake to verify our key. We create a wordlist and/or download some popular ones from the internet like the rockyou.txt. This method is known as the Dictionary Bruteforce attack. If the wordlist contains the password, it outputs the password. aircrack-ng wpa wpa_handshake.cap -w rockyou.txt 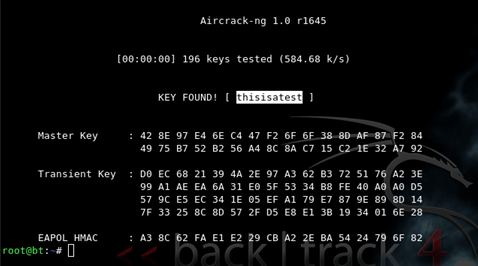
|
【本文地址】