华为防火墙的策略路由 |
您所在的位置:网站首页 › 防火墙如何做策略 › 华为防火墙的策略路由 |
华为防火墙的策略路由
|
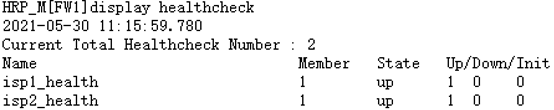
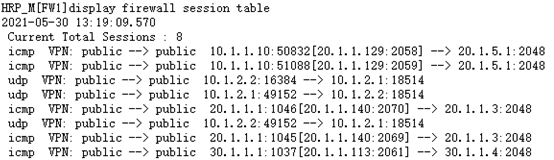
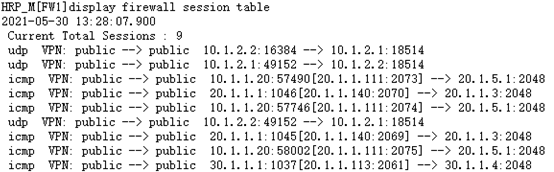
1.配置内网及DMZ区域的IP地址 [FW1-GigabitEthernet1/0/1]ip add 10.1.1.1 24 [FW1-GigabitEthernet1/0/3]ip add 10.1.2.1 24 [FW2-GigabitEthernet1/0/1]ip add 10.1.1.2 24 [FW2-GigabitEthernet1/0/3]ip add 10.1.2.2 24 2.配置外网的IP地址及其连通性 [FW1-GigabitEthernet1/0/2]ip add 20.1.1.1 24 [FW1-GigabitEthernet1/0/4]ip add 30.1.1.1 24 [FW2-GigabitEthernet1/0/2]ip add 30.1.2.2 24 [FW2-GigabitEthernet1/0/4]ip add 20.1.2.2 24 [ISP1-GigabitEthernet0/0/0]ip add 20.1.1.3 24 [ISP1-GigabitEthernet0/0/1]ip add 20.1.5.3 24 [ISP1-GigabitEthernet0/0/2]ip add 20.1.2.3 24 [ISP2-GigabitEthernet0/0/0]ip add 30.1.2.4 24 [ISP2-GigabitEthernet0/0/1]ip add 20.1.5.4 24 [ISP2-GigabitEthernet0/0/2]ip add 30.1.1.4 24 [ISP1-GigabitEthernet0/0/1]vrrp vrid 1 virtual-ip 20.1.5.254 [ISP2-GigabitEthernet0/0/1]vrrp vrid 1 virtual-ip 20.1.5.254 [ISP1]ospf [ISP1-ospf-1]area 0 [ISP1-ospf-1-area-0.0.0.0]net 20.1.1.0 0.0.0.255 [ISP1-ospf-1-area-0.0.0.0]net 20.1.2.0 0.0.0.255 [ISP1-ospf-1-area-0.0.0.0]net 20.1.5.0 0.0.0.255 [ISP2]ospf [ISP2-ospf-1]area 0 [ISP2-ospf-1-area-0.0.0.0]net 30.1.1.0 0.0.0.255 [ISP2-ospf-1-area-0.0.0.0]net 30.1.2.0 0.0.0.255 [ISP2-ospf-1-area-0.0.0.0]net 20.1.5.0 0.0.0.255 3.防火墙接口加入各自区域并放行ping命令,便于测试 [FW1]firewall zone trust [FW1-zone-trust]add interface g1/0/1 [FW1]firewall zone untrust [FW1-zone-untrust]add interface g1/0/2 [FW1-zone-untrust]add interface g1/0/4 [FW1]firewall zone dmz [FW1-zone-dmz]add interface g1/0/3 [FW1-GigabitEthernet1/0/1]service-manage ping permit [FW1-GigabitEthernet1/0/2]service-manage ping permit [FW1-GigabitEthernet1/0/3]service-manage ping permit [FW1-GigabitEthernet1/0/4]service-manage ping permit [FW2]firewall zone trust [FW2-zone-trust]add interface g1/0/1 [FW2]firewall zone untrust [FW2-zone-untrust]add interface g1/0/2 [FW2-zone-untrust]add interface g1/0/4 [FW2]firewall zone dmz [FW2-zone-dmz]add interface g1/0/3 [FW2-GigabitEthernet1/0/1]service-manage ping permit [FW2-GigabitEthernet1/0/2]service-manage ping permit [FW2-GigabitEthernet1/0/3]service-manage ping permit [FW2-GigabitEthernet1/0/4]service-manage ping permit 4.配置默认出口路由 [FW1]ip route-static 0.0.0.0 0.0.0.0 20.1.1.3 [FW1]ip route-static 0.0.0.0 0.0.0.0 30.1.1.4 preference 100 [FW2]ip route-static 0.0.0.0 0.0.0.0 20.1.2.3 [FW2]ip route-static 0.0.0.0 0.0.0.0 30.1.2.4 preference 100 5.配置源NAT,使内网能够访问外网 [FW1]nat address-group nat_fw1 [FW1-address-group-nat_fw1]section 20.1.1.100 20.1.1.200 [FW1]nat-policy [FW1-policy-nat-rule-source_fw1]source-zone trust local [FW1-policy-nat-rule-source_fw1]destination-zone untrust [FW1-policy-nat-rule-source_fw1]action source-nat address-group nat_fw1 [FW2]nat address-group nat_fw2 [FW2-address-group-nat_fw2]section 30.1.1.100 30.1.1.200 [FW2]nat-policy [FW2-policy-nat]rule name source_fw2 [FW2-policy-nat-rule-source_fw2]source-zone local trust [FW2-policy-nat-rule-source_fw2]destination-zone untrust [FW2-policy-nat-rule-source_fw2]action source-nat address-group nat_fw2 6.配置IP-link功能 [FW1]ip-link check enable [FW1] ip-link name ip_link1 [FW1-iplink-ip_link1]destination 20.1.1.3 interface GigabitEthernet 1/0/2 mode icmp [FW1-iplink-ip_link1]destination 30.1.1.4 interface GigabitEthernet 1/0/3 mode icmp [FW2]ip-link check enable [FW2] ip-link name ip_link2 [FW2-iplink-ip_link2]destination 30.1.2.4 interface GigabitEthernet 1/0/2 mode icmp [FW2-iplink-ip_link2]destination 20.1.2.3 interface GigabitEthernet 1/0/4 mode icmp 7.配置健康检查功能 [FW1]healthcheck enable [FW1]healthcheck name isp1_health [FW1-healthcheck-isp1_health]destination 20.1.1.3 interface g1/0/2 protocol icmp [FW1]healthcheck name isp2_health [FW1-healthcheck-isp2_health]destination 30.1.1.4 interface g1/0/4 protocol icmp [FW2]healthcheck enable [FW2]healthcheck name isp1_health [FW2-healthcheck-isp1_health]destination 20.1.2.3 interface g1/0/4 protocol icmp [FW2]healthcheck name isp2_health [FW2-healthcheck-isp2_health]destination 30.1.2.4 interface g1/0/2 protocol icmp 8.配置接口带宽 [FW1-GigabitEthernet1/0/2]healthcheck isp1_health [FW1-GigabitEthernet1/0/2]gateway 20.1.1.3 [FW1-GigabitEthernet1/0/2]bandwidth ingress 50000 threshold 90 [FW1-GigabitEthernet1/0/2]bandwidth egress 50000 threshold 90 [FW1-GigabitEthernet1/0/4]healthcheck isp2_health [FW1-GigabitEthernet1/0/4]gateway 30.1.1.4 [FW1-GigabitEthernet1/0/4]bandwidth ingress 50000 threshold 90 [FW1-GigabitEthernet1/0/4]bandwidth egress 50000 threshold 90 [FW2-GigabitEthernet1/0/4]healthcheck isp1_health [FW2-GigabitEthernet1/0/4]gateway 20.1.2.3 [FW2-GigabitEthernet1/0/4]bandwidth ingress 50000 threshold 90 [FW2-GigabitEthernet1/0/4]bandwidth egress 50000 threshold 90 [FW2-GigabitEthernet1/0/2]healthcheck isp2_health [FW1-GigabitEthernet1/0/2]gateway 30.1.2.4 [FW1-GigabitEthernet1/0/2]bandwidth ingress 50000 threshold 90 [FW1-GigabitEthernet1/0/2]bandwidth egress 50000 threshold 90 9.配置全局选路策略 [FW1]link-interface 0 name ISP1 [FW1-linkif-0]interface g1/0/2 next-hop 20.1.1.3 [FW1-linkif-0]healthcheck isp1_health [FW1]link-interface 1 name ISP2 [FW1-linkif-1]interface g1/0/4 next-hop 30.1.1.3 [FW1-linkif-1]healthcheck isp2_health [FW1]multi-linkif [FW1-multi-linkif]mode priority-of-link-quality [FW1-multi-linkif]priority-of-link-quality parameter loss [FW1-multi-linkif]priority-of-link-quality protocol tcp-simple [FW1-multi-linkif]add linkif ISP1 [FW1-multi-linkif]add linkif ISP2 [FW2]link-interface 0 name ISP1 [FW2-linkif-0]interface g1/0/4 next-hop 20.1.2.3 [FW2-linkif-0]healthcheck isp1_health [FW2]link-interface 1 name ISP2 [FW2-linkif-1]interface g1/0/2 next-hop 30.1.2.4 [FW2-linkif-1]healthcheck isp2_health [FW2]multi-linkif [FW2-multi-linkif]mode priority-of-link-quality [FW2-multi-linkif]priority-of-link-quality parameter loss [FW2-multi-linkif]priority-of-link-quality protocol tcp-simple [FW2-multi-linkif]add linkif ISP1 [FW2-multi-linkif]add linkif ISP2 10.配置防火墙双机热备并联动IP-LINK [FW1-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 10.1.1.254 active [FW1-GigabitEthernet1/0/1]vrrp virtual-mac enable [FW1]hrp enable HRP_S[FW1]hrp interface g1/0/3 remote 10.1.2.2 HRP_M[FW1]hrp track ip-link ip_link1 [FW2-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 10.1.1.254 standby [FW2-GigabitEthernet1/0/1]vrrp virtual-mac enable [FW2]hrp enable HRP_S[FW2]hrp interface g1/0/3 remote 10.1.2.1 HRP_S[FW2]hrp track ip-link ip_link2 11.配置策略路由 [FW1]policy-based-route [FW1-policy-pbr]rule name to_ISP1 [FW1-policy-pbr-rule-to_ISP1]source-zone trust [FW1-policy-pbr-rule-to_ISP1]source-address 10.1.1.10 32 [FW1-policy-pbr-rule-to_ISP1]action pbr egress-interface g 1/0/2 next-hop 20.1.1.3 [FW1-policy-pbr]rule name to_ISP2 [FW1-policy-pbr-rule-to_ISP2]source-zone trust [FW1-policy-pbr-rule-to_ISP2]source-zone trust [FW1-policy-pbr-rule-to_ISP2]source-address 10.1.1.20 32 [FW1-policy-pbr-rule-to_ISP2]action pbr egress-interface g1/0/4 next-hop 30.1.1.4 [FW2]policy-based-route [FW2-policy-pbr]rule name to_ISP1 [FW2-policy-pbr-rule-to_ISP1]source-zone trust [FW2-policy-pbr-rule-to_ISP1]source-address 10.1.1.10 32 [FW2-policy-pbr-rule-to_ISP1]action pbr egress-interface g1/0/4 next-hop 20.1.2.3 [FW2-policy-pbr]rule name to_ISP2 [FW2-policy-pbr-rule-to_ISP2]source-zone trust [FW2-policy-pbr-rule-to_ISP2]source-address 10.1.1.20 32 [FW2-policy-pbr-rule-to_ISP2]action pbr egress-interface g1/0/2 next-hop 30.1.2.4 12.配置安全策略 [FW1]security-policy [FW1-policy-security]rule name OUT [FW1-policy-security-rule-OUT]source-zone trust local [FW1-policy-security-rule-OUT]destination-zone untrust [FW1-policy-security-rule-OUT]action permit [FW2]security-policy [FW2-policy-security]rule name OUT [FW2-policy-security-rule-OUT]source-zone trust local [FW2-policy-security-rule-OUT]destination-zone untrust [FW2-policy-security-rule-OUT]action permit 13.验证 PC1和PC2都可以ping通服务器
|
【本文地址】
今日新闻 |
推荐新闻 |