看我如何黑进邻居的电视 |
您所在的位置:网站首页 › 怎么把监控黑掉 › 看我如何黑进邻居的电视 |
看我如何黑进邻居的电视
|
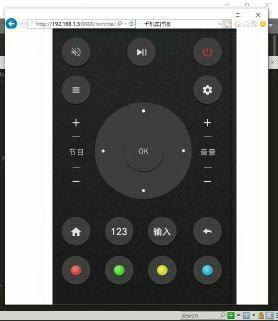
标题只是个玩笑,请大家不要模仿。本文的目标是提高大家对互联网设备安全的重视。 首先要接入邻居的wifi。关于如何破解wifi,这里我提供三个方法: 用reaver跑pin码。但是现在拉宽带送的无线路由器都跑不了了,成功率不算高。再加上现在家家户户都有一个质量参差不齐的路由器,信号干扰很严重,跑pin的速度不是很理想。wifi万能钥匙,对于缺乏网络安全常识的邻居来说,这招很好用。已root的手机连上wifi后,通过文件管理器打开data/misc/wifi/wpa_supplicant.conf文件,看到ssid和对应的psk就是wifi名称和密码了。抓握手包。目前常规配置的电脑跑弱密码的话效率还不错,如果配合一些你对邻居做社工工作的定制化字典,成功率也挺高的。也可以花几块钱拿去淘宝跑。不过对于这种看不到进度条的随缘工作我是没有什么耐心的。问邻居。没错,你要是个可爱的男孩子,去邻居家蹭饭的时候问下密码最简单了得到密码后,电脑就可以连接了。当然,以下的工具在安卓手机上也是可以完成的。见我关于手机上安装linux环境的文章。 先看一下dhcp分配给你的ip,然后nmap扫码一下C段。比如nmap -sP -T5 192.168.1.1/24 扫出来设备为Unknown的,可以去mac地址厂商查询网站查询一下。比如我这次的目标,nmap扫描出来的mac就是unknow,然后去一些mac厂商查询的网站(度娘一下一大堆?)查询一下才知道是创维电视。 再对这个电视的ip扫一下 nmap -A -Pn -T5 192.168.1.3 Starting Nmap 7.70 ( https://nmap.org ) at 2018-11-18 01:15 ?D1ú±ê×?ê±?? Nmap scan report for 192.168.1.3 Host is up (0.0029s latency). Not shown: 995 closed ports PORT STATE SERVICE VERSION 2010/tcp open search? 7100/tcp open font-service? 8087/tcp open http Pcounter httpd |_http-title: Site doesn't have a title (text/plain). 8200/tcp open trivnet1? | fingerprint-strings: | DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NULL, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, WMSRequest, X11Probe: | HTTP/1.1 200 OK |_ Content-Type:text/html;charset:GBK 8888/tcp open sun-answerbook? | fingerprint-strings: | FourOhFourRequest: | HTTP/1.0 500 Internal Server Error | Access-Control-Allow-Headers: Content-Type,Accept,Origin,No-Cache | Access-Control-Allow-Origin: * | Access-Control-Allow-Credentials: true | Date: Sat, 17 Nov 2018 17:15:25 GMT+00:00 | Server: CMCC Http Server | Content-Length: 0 | GenericLines: | HTTP/1.0 400 Bad Request | Date: Sat, 17 Nov 2018 17:15:31 GMT+00:00 | Server: CMCC Http Server | Content-Length: 22 | Content-Type: text/plain; charset=US-ASCII | Connection: Close | Invalid request line: | GetRequest: | HTTP/1.0 200 OK | Access-Control-Allow-Headers: Content-Type,Accept,Origin,No-Cache | Access-Control-Allow-Origin: * | Access-Control-Allow-Credentials: true | Date: Sat, 17 Nov 2018 17:15:25 GMT+00:00 | Server: CMCC Http Server | Content-Length: 212 | Content-Type: text/html; charset=UTF-8 | | | | | | | | window.location.href="./remote/index.html"; | | | | | | HTTPOptions: | HTTP/1.0 200 OK | Access-Control-Allow-Headers: Content-Type,Accept,Origin,No-Cache | Access-Control-Allow-Origin: * | Access-Control-Allow-Credentials: true | Date: Sat, 17 Nov 2018 17:15:25 GMT+00:00 | Server: CMCC Http Server | Content-Length: 0 | LSCP: | HTTP/1.0 400 Bad Request | Date: Sat, 17 Nov 2018 17:15:31 GMT+00:00 | Server: CMCC Http Server | Content-Length: 35 | Content-Type: text/plain; charset=US-ASCII | Connection: Close |_ valid protocol version: INFO 3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service : ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port2010-TCP:V=7.70%I=7%D=11/18%Time=5BF04CAC%P=i686-pc-windows-windows SF:%r(NULL,5,"\x12V\x124c")%r(GenericLines,5,"\x12V\x124c")%r(GetRequest,5 SF:,"\x12V\x124c")%r(RTSPRequest,5,"\x12V\x124c")%r(DNSVersionBindReqTCP,5 SF:,"\x12V\x124c")%r(Help,5,"\x12V\x124c")%r(TLSSessionReq,5,"\x12V\x124c" SF:)%r(SMBProgNeg,5,"\x12V\x124c")%r(FourOhFourRequest,5,"\x12V\x124c")%r( SF:LDAPSearchReq,5,"\x12V\x124c")%r(SIPOptions,5,"\x12V\x124c")%r(LANDesk- SF:RC,5,"\x12V\x124c")%r(NCP,5,"\x12V\x124c")%r(JavaRMI,5,"\x12V\x124c")%r SF:(oracle-tns,5,"\x12V\x124c")%r(afp,5,"\x12V\x124c"); ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port8200-TCP:V=7.70%I=7%D=11/18%Time=5BF04CA6%P=i686-pc-windows-windows SF:%r(NULL,34,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html;charset:GBK\ SF:n\n")%r(GenericLines,35,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html SF:;charset:GBK\n\n\n")%r(GetRequest,35,"HTTP/1\.1\x20200\x20OK\nContent-T SF:ype:text/html;charset:GBK\n\n\n")%r(HTTPOptions,35,"HTTP/1\.1\x20200\x2 SF:0OK\nContent-Type:text/html;charset:GBK\n\n\n")%r(RTSPRequest,35,"HTTP/ SF:1\.1\x20200\x20OK\nContent-Type:text/html;charset:GBK\n\n\n")%r(RPCChec SF:k,34,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html;charset:GBK\n\n")% SF:r(DNSVersionBindReqTCP,34,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/ht SF:ml;charset:GBK\n\n")%r(DNSStatusRequestTCP,34,"HTTP/1\.1\x20200\x20OK\n SF:Content-Type:text/html;charset:GBK\n\n")%r(Help,35,"HTTP/1\.1\x20200\x2 SF:0OK\nContent-Type:text/html;charset:GBK\n\n\n")%r(SSLSessionReq,35,"HTT SF:P/1\.1\x20200\x20OK\nContent-Type:text/html;charset:GBK\n\n\n")%r(TLSSe SF:ssionReq,35,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html;charset:GBK SF:\n\n\n")%r(Kerberos,35,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html; SF:charset:GBK\n\n\n")%r(SMBProgNeg,34,"HTTP/1\.1\x20200\x20OK\nContent-Ty SF:pe:text/html;charset:GBK\n\n")%r(X11Probe,34,"HTTP/1\.1\x20200\x20OK\nC SF:ontent-Type:text/html;charset:GBK\n\n")%r(FourOhFourRequest,35,"HTTP/1\ SF:.1\x20200\x20OK\nContent-Type:text/html;charset:GBK\n\n\n")%r(LPDString SF:,35,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html;charset:GBK\n\n\n") SF:%r(LDAPSearchReq,35,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html;cha SF:rset:GBK\n\n\n")%r(LDAPBindReq,34,"HTTP/1\.1\x20200\x20OK\nContent-Type SF::text/html;charset:GBK\n\n")%r(SIPOptions,35,"HTTP/1\.1\x20200\x20OK\nC SF:ontent-Type:text/html;charset:GBK\n\n\n")%r(LANDesk-RC,34,"HTTP/1\.1\x2 SF:0200\x20OK\nContent-Type:text/html;charset:GBK\n\n")%r(TerminalServer,3 SF:4,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html;charset:GBK\n\n")%r(N SF:CP,34,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html;charset:GBK\n\n") SF:%r(NotesRPC,34,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html;charset: SF:GBK\n\n")%r(JavaRMI,34,"HTTP/1\.1\x20200\x20OK\nContent-Type:text/html; SF:charset:GBK\n\n")%r(WMSRequest,34,"HTTP/1\.1\x20200\x20OK\nContent-Type SF::text/html;charset:GBK\n\n"); ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port8888-TCP:V=7.70%I=7%D=11/18%Time=5BF04CAB%P=i686-pc-windows-windows SF:%r(GetRequest,1F4,"HTTP/1\.0\x20200\x20OK\r\nAccess-Control-Allow-Heade SF:rs:\x20Content-Type,Accept,Origin,No-Cache\r\nAccess-Control-Allow-Orig SF:in:\x20\*\r\nAccess-Control-Allow-Credentials:\x20true\r\nDate:\x20Sat, SF:\x2017\x20Nov\x202018\x2017:15:25\x20GMT\+00:00\r\nServer:\x20CMCC\x20H SF:ttp\x20Server\r\nContent-Length:\x20212\r\nContent-Type:\x20text/html;\ SF:x20charset=UTF-8\r\n\r\n\n\n\n\x20\x20\x20\x20\n\x20\x20\x20\x20\xe6\x89\x8b\xe6\x9c\xba\xe9\x81\xa5\xe6\x8e\xa7\xe5\x99\xa8\n SF:\x20\x20\x20\x20\n\x20\x20\x20\x20\x20\x20\x20\x20window\.locat SF:ion\.href=\"\./remote/index\.html\";\n\x20\x20\x20\x20\n\n\n\n\n")%r(HTTPOptions,F6,"HTTP/1\.0\x20200\x20O SF:K\r\nAccess-Control-Allow-Headers:\x20Content-Type,Accept,Origin,No-Cac SF:he\r\nAccess-Control-Allow-Origin:\x20\*\r\nAccess-Control-Allow-Creden SF:tials:\x20true\r\nDate:\x20Sat,\x2017\x20Nov\x202018\x2017:15:25\x20GMT SF:\+00:00\r\nServer:\x20CMCC\x20Http\x20Server\r\nContent-Length:\x200\r\ SF:n\r\n")%r(FourOhFourRequest,109,"HTTP/1\.0\x20500\x20Internal\x20Server SF:\x20Error\r\nAccess-Control-Allow-Headers:\x20Content-Type,Accept,Origi SF:n,No-Cache\r\nAccess-Control-Allow-Origin:\x20\*\r\nAccess-Control-Allo SF:w-Credentials:\x20true\r\nDate:\x20Sat,\x2017\x20Nov\x202018\x2017:15:2 SF:5\x20GMT\+00:00\r\nServer:\x20CMCC\x20Http\x20Server\r\nContent-Length: SF:\x200\r\n\r\n")%r(LSCP,D7,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\ SF:x20Sat,\x2017\x20Nov\x202018\x2017:15:31\x20GMT\+00:00\r\nServer:\x20CM SF:CC\x20Http\x20Server\r\nContent-Length:\x2035\r\nContent-Type:\x20text/ SF:plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\nNot\x20a\x20v SF:alid\x20protocol\x20version:\x20\x20INFO")%r(GenericLines,CA,"HTTP/1\.0 SF:\x20400\x20Bad\x20Request\r\nDate:\x20Sat,\x2017\x20Nov\x202018\x2017:1 SF:5:31\x20GMT\+00:00\r\nServer:\x20CMCC\x20Http\x20Server\r\nContent-Leng SF:th:\x2022\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnec SF:tion:\x20Close\r\n\r\nInvalid\x20request\x20line:\x20"); MAC Address: C8这里打上马赛克59 (Unknown) Device type: general purpose Running: Linux 2.6.X|3.X OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 OS details: Linux 2.6.32 - 3.10 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 2.93 ms 192.168.1.3 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 170.76 seconds发现8888端口是个奇怪的服务,看到这段代码: | window.location.href="./remote/index.html"; |用浏览器连一下http://192.168.1.3/就自动定位到http://192.168.1.3/remote/index.html。看图:
居然是遥控器,而且没有要求任何验证。使用burpsuite重放攻击了一下,观察返回值是有变化的。说明遥控器是生效的。也就是说我现在可以控制邻居的电视了。 好害怕。 然后我在另一个网络中发现了监控设备,可能是楼道里的闭路电视。目前发现了漏洞,还没找到能成功利用的exp。 扫描和利用的过程到此结束。而文章的目的从这里开始。 现在很多智能家居设备,然而对于普通用户来说,这些设备的安全性却不得而知。用户信任厂商而购买了他们的产品,而厂商却不打算对卖出的产品负责,安全性不重视,把客户的隐私暴露在光天化日之下。 身边很多朋友执意要买这些没有安全保障的互联网设备,我劝也没用。希望这篇文章可以引起大家的重视。 |
【本文地址】
今日新闻 |
推荐新闻 |