麒麟KYSEC使用方法06 |
您所在的位置:网站首页 › uos密码错误锁定时间 › 麒麟KYSEC使用方法06 |
麒麟KYSEC使用方法06
|
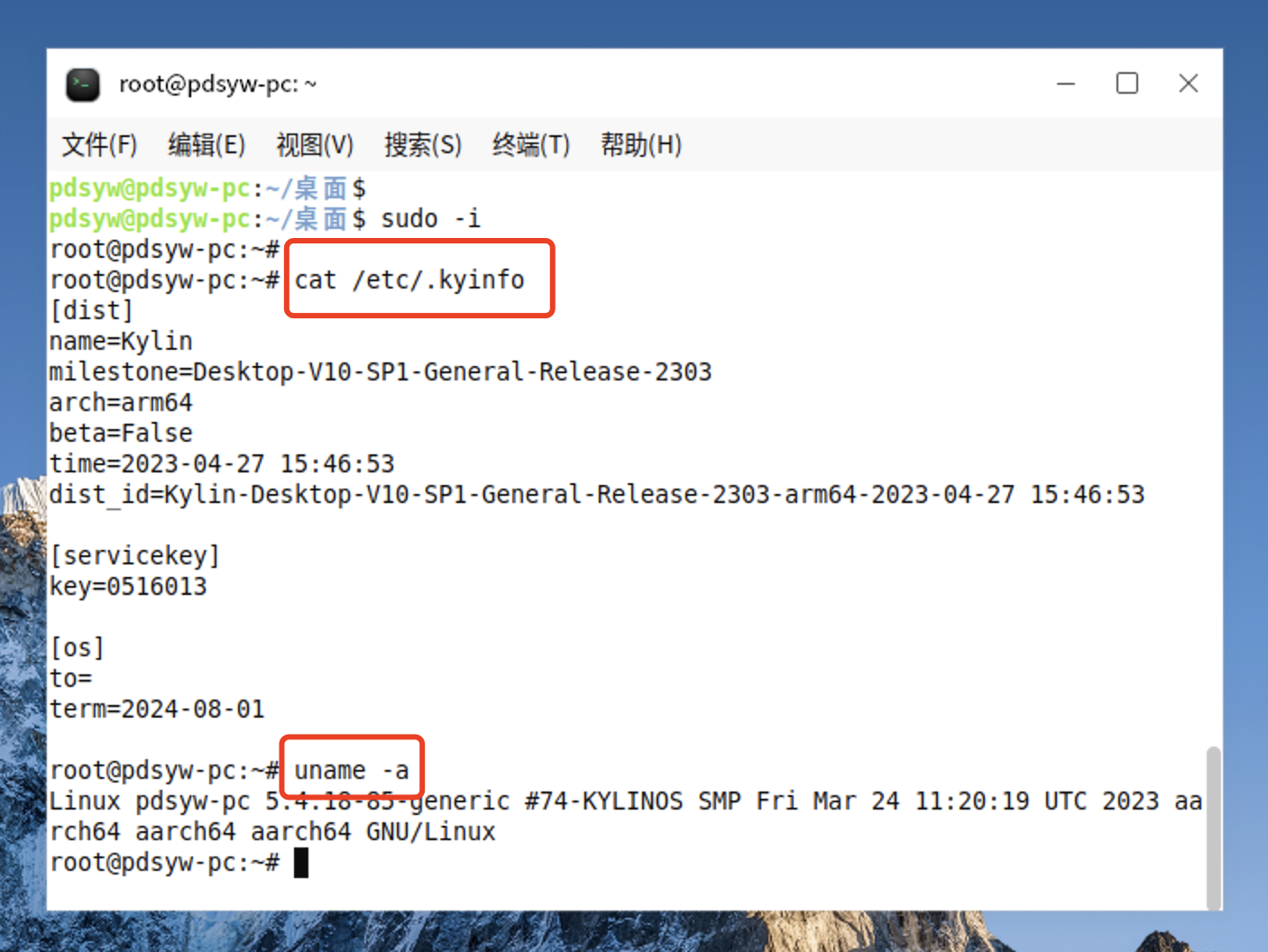
原文链接:麒麟KYSEC使用方法06-命令设置账户锁定 hello,大家好啊,今天给大家带来麒麟KYLINOS的kysec使用方法系列文章第六篇内容----使用命令设置账户锁定,账户锁定策略有一个文件需要修改,common-auth,今天给大家介绍一下使用命令设置账户锁定的文章,欢迎大家点个赞并点个在看。关注我吧! 1、查看系统信息 pdsyw@pdsyw-pc:~/桌面$ sudo -i root@pdsyw-pc:~# root@pdsyw-pc:~# cat /etc/.kyinfo [dist] name=Kylin milestone=Desktop-V10-SP1-General-Release-2303 arch=arm64 beta=False time=2023-04-27 15:46:53 dist_id=Kylin-Desktop-V10-SP1-General-Release-2303-arm64-2023-04-27 15:46:53 [servicekey] key=0516013 [os] to= term=2024-08-01 root@pdsyw-pc:~# uname -a Linux pdsyw-pc 5.4.18-85-generic #74-KYLINOS SMP Fri Mar 24 11:20:19 UTC 2023 aarch64 aarch64 aarch64 GNU/Linux root@pdsyw-pc:~#
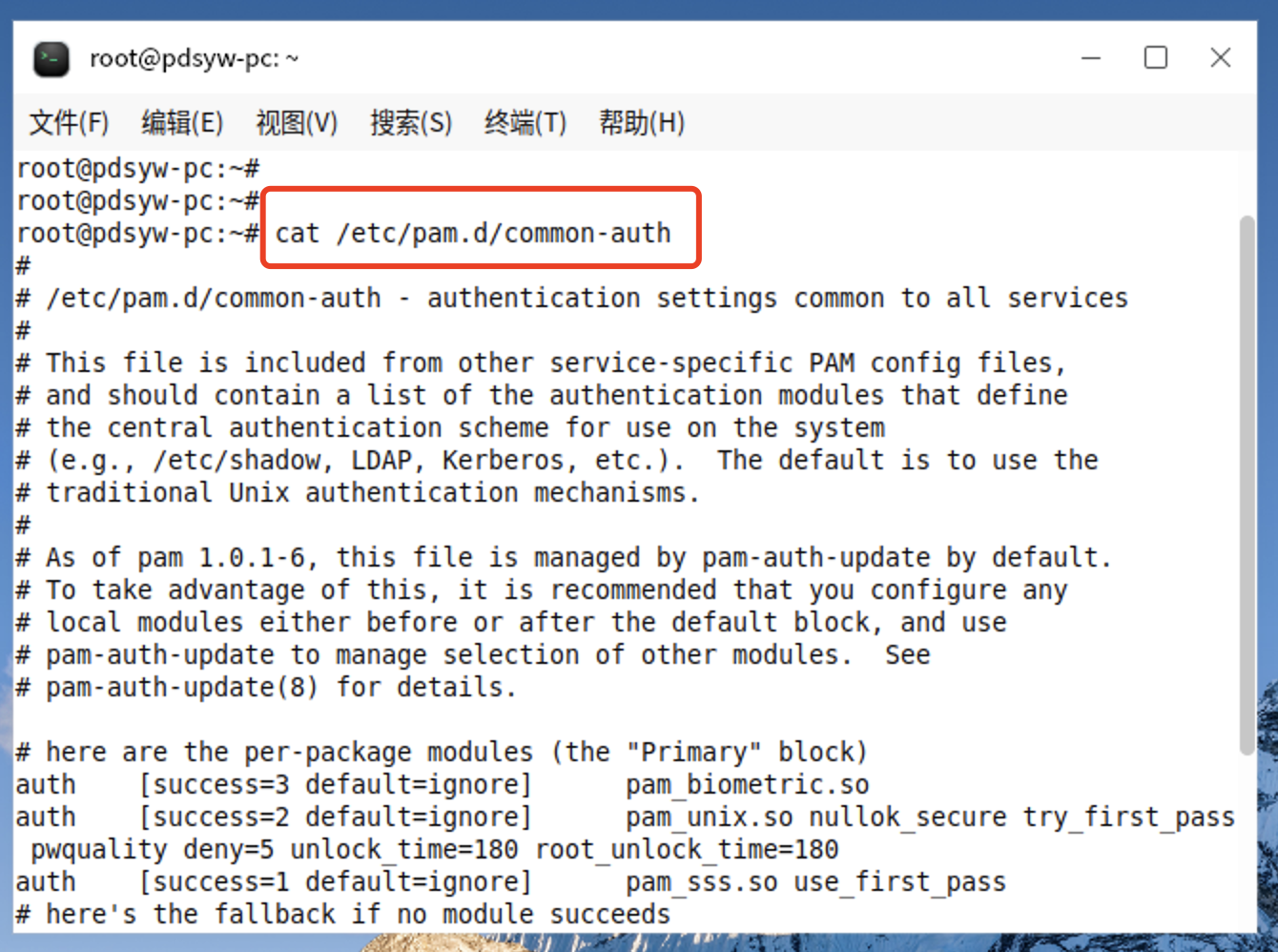
2、查看common-auth原文件 root@pdsyw-pc:~# cat /etc/pam.d/common-auth # # /etc/pam.d/common-auth - authentication settings common to all services # # This file is included from other service-specific PAM config files, # and should contain a list of the authentication modules that define # the central authentication scheme for use on the system # (e.g., /etc/shadow, LDAP, Kerberos, etc.). The default is to use the # traditional Unix authentication mechanisms. # # As of pam 1.0.1-6, this file is managed by pam-auth-update by default. # To take advantage of this, it is recommended that you configure any # local modules either before or after the default block, and use # pam-auth-update to manage selection of other modules. See # pam-auth-update(8) for details. # here are the per-package modules (the "Primary" block) auth [success=3 default=ignore] pam_biometric.so auth [success=2 default=ignore] pam_unix.so nullok_secure try_first_pass pwquality deny=5 unlock_time=180 root_unlock_time=180 auth [success=1 default=ignore] pam_sss.so use_first_pass # here's the fallback if no module succeeds auth requisite pam_deny.so # prime the stack with a positive return value if there isn't one already; # this avoids us returning an error just because nothing sets a success code # since the modules above will each just jump around auth required pam_permit.so # and here are more per-package modules (the "Additional" block) # end of pam-auth-update config root@pdsyw-pc:~#
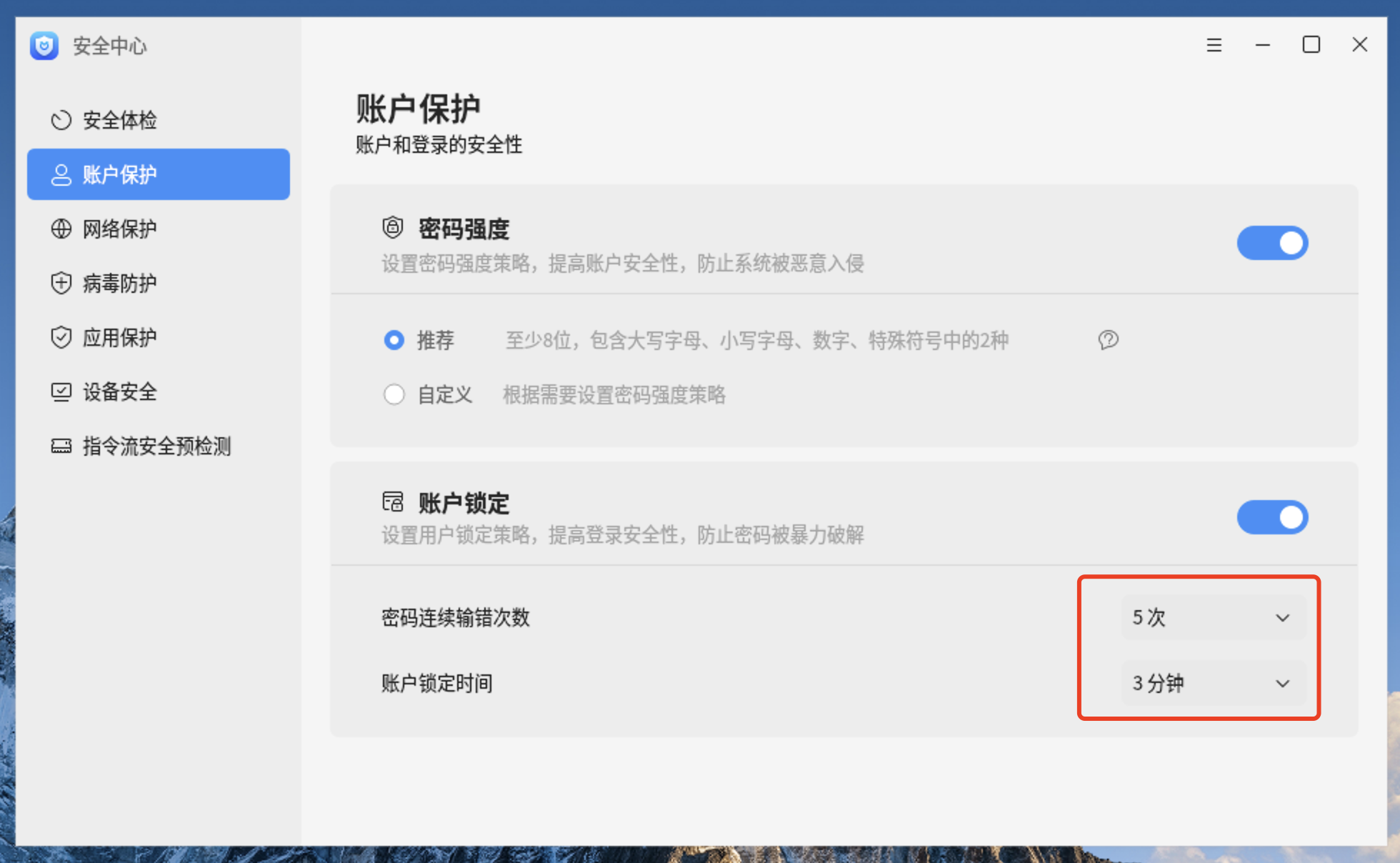
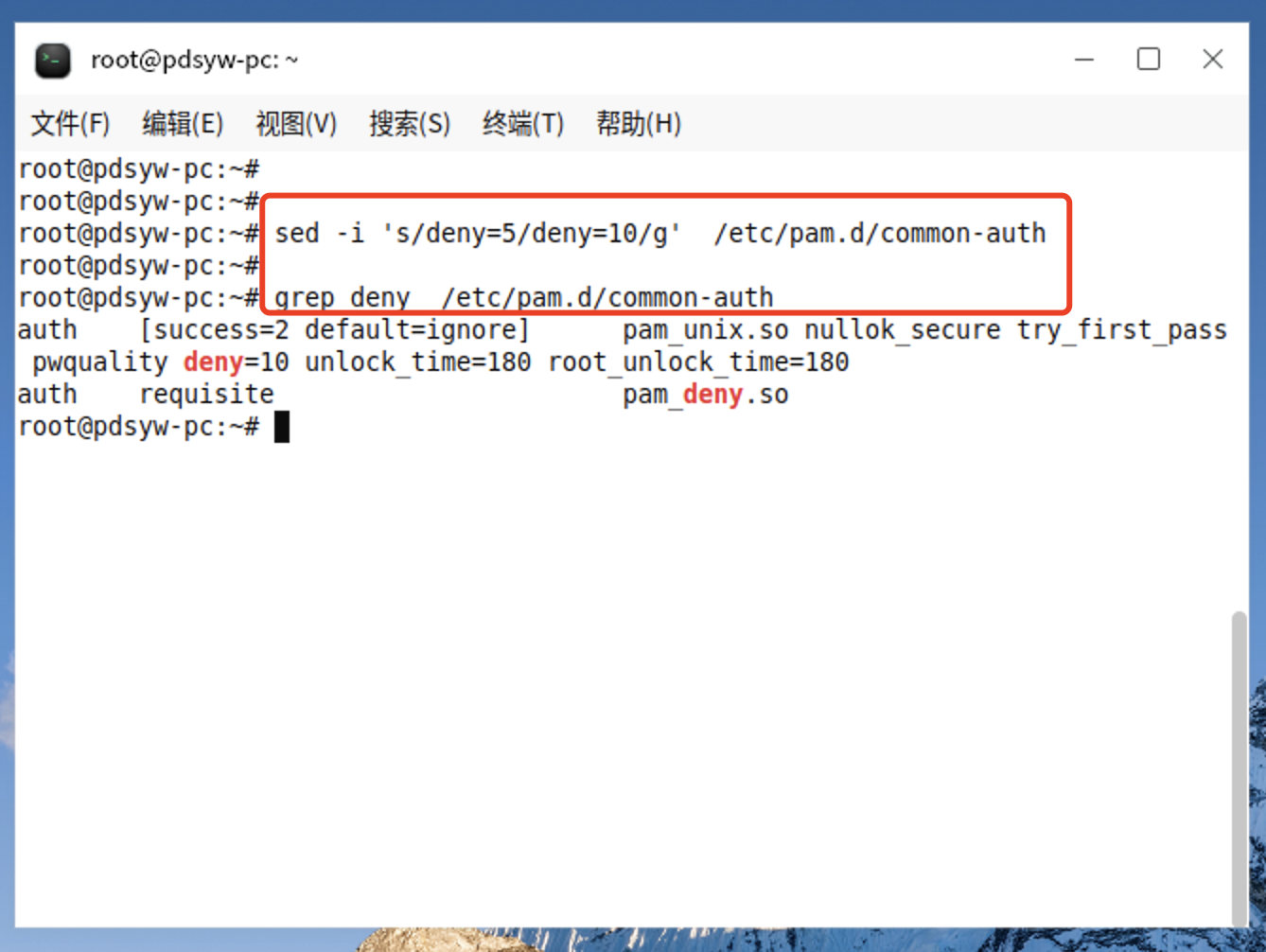
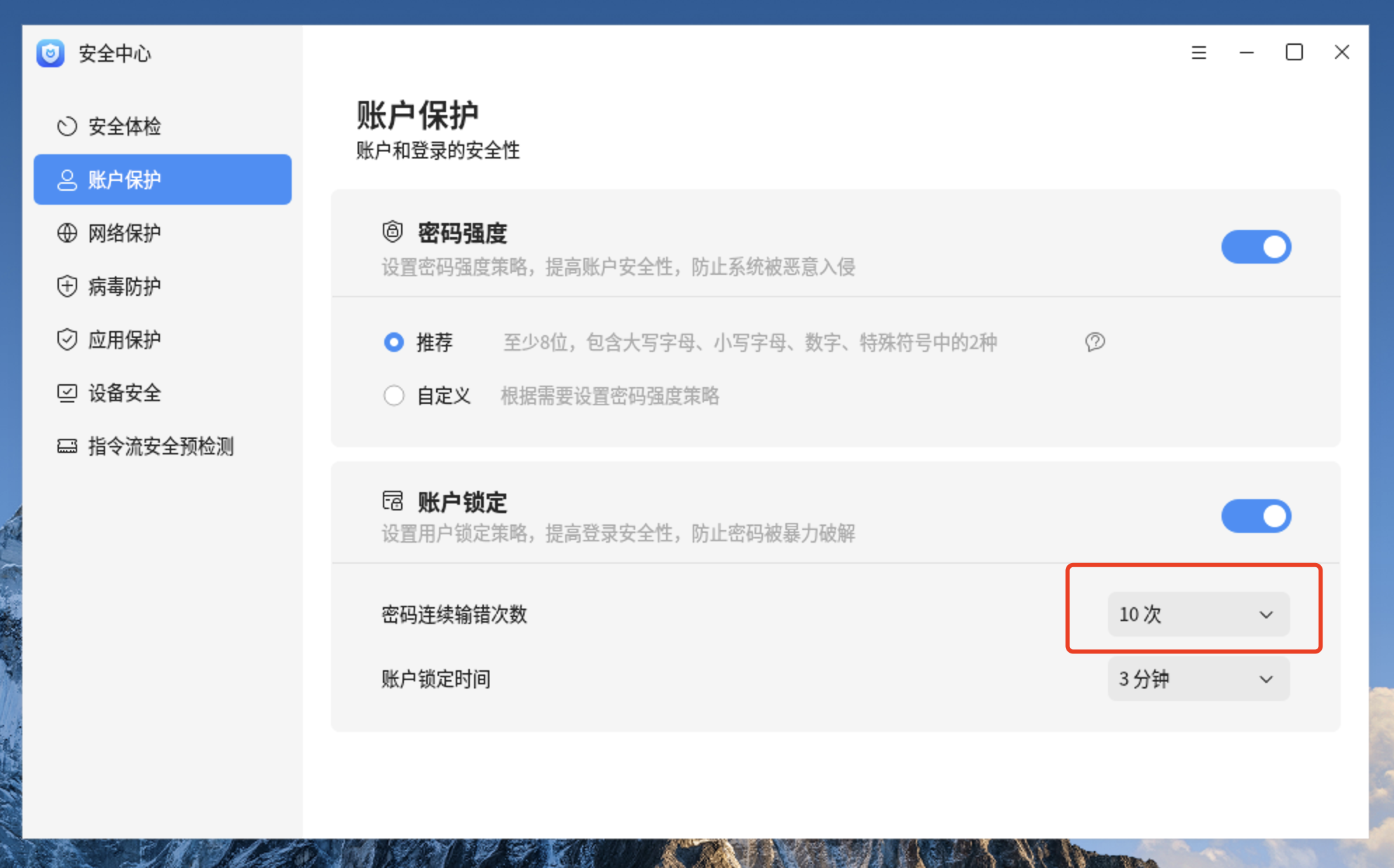
3、查看账户锁定的策略情况 4、更改密码连续输错次数为10次 root@pdsyw-pc:~# sed -i 's/deny=5/deny=10/g' /etc/pam.d/common-auth root@pdsyw-pc:~# root@pdsyw-pc:~# grep deny /etc/pam.d/common-auth auth [success=2 default=ignore] pam_unix.so nullok_secure try_first_pass pwquality deny=10 unlock_time=180 root_unlock_time=180 auth requisite pam_deny.so root@pdsyw-pc:~#
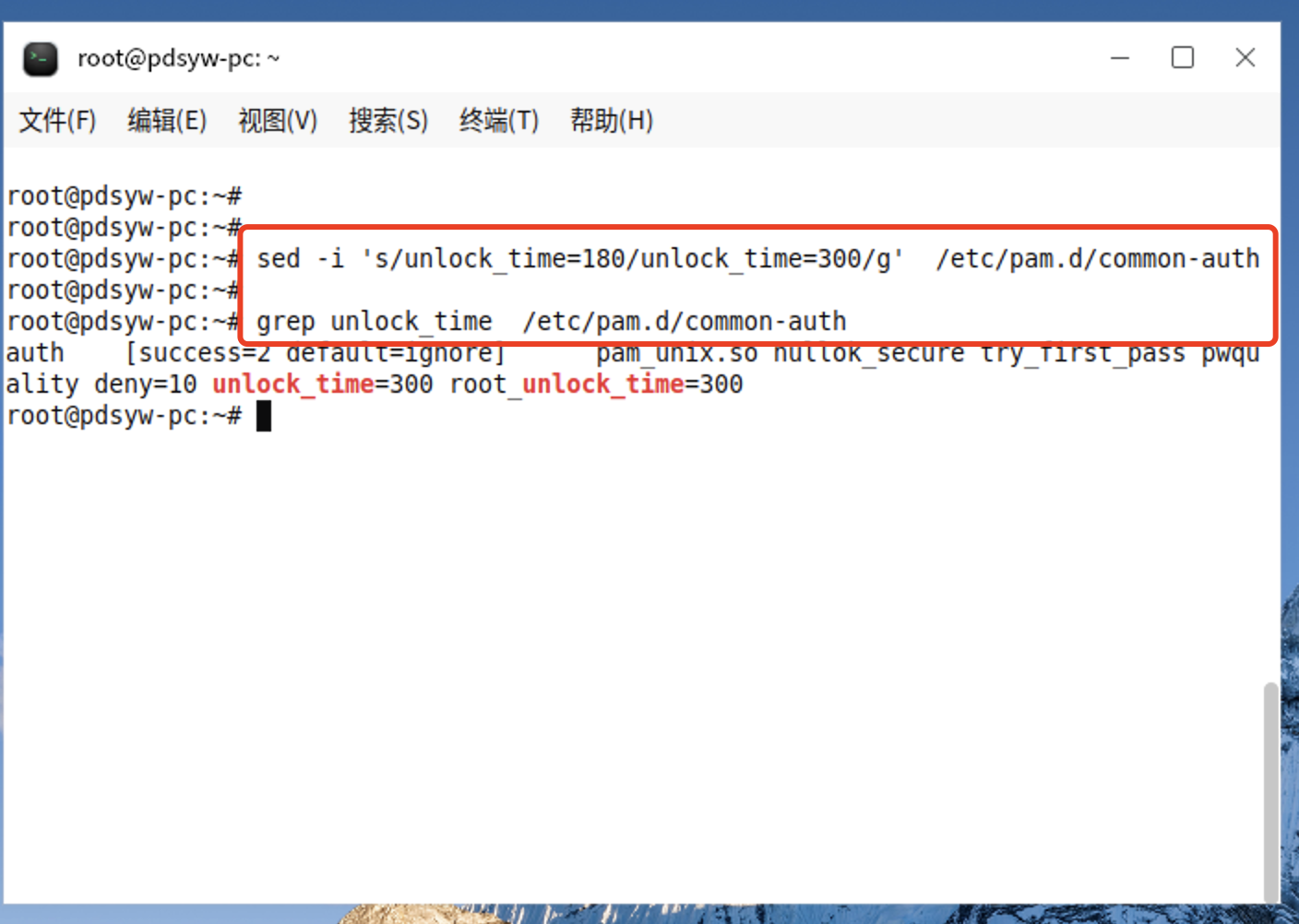
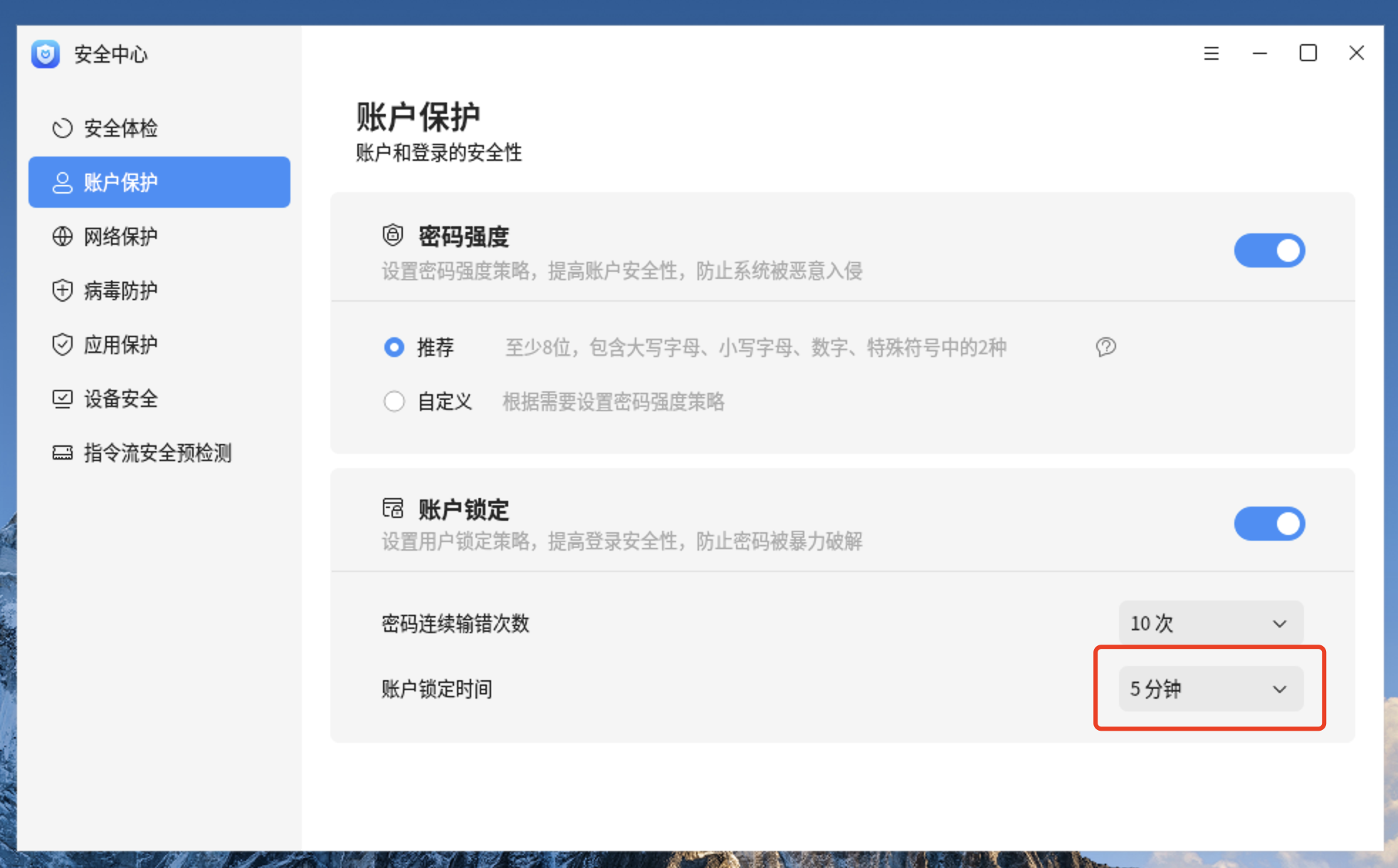
5、更改后的情况 6、更改账户锁定时间为5分钟 root@pdsyw-pc:~# sed -i 's/unlock_time=180/unlock_time=300/g' /etc/pam.d/common-authroot@pdsyw-pc:~# root@pdsyw-pc:~# grep unlock_time /etc/pam.d/common-auth auth [success=2 default=ignore] pam_unix.so nullok_secure try_first_pass pwquality deny=10 unlock_time=300 root_unlock_time=300 root@pdsyw-pc:~#
7、更改后的情况 |
【本文地址】
今日新闻 |
推荐新闻 |