IPSec 隧道技术 |
您所在的位置:网站首页 › ipsec加密算法 › IPSec 隧道技术 |
IPSec 隧道技术
|
IPSec 隧道技术–基础实验配置 IPSec 简介(Internet Protocol Security)是IETF(Internet Engineering Task Force)制定的一组开放的网络安全协议,在IP层通过数据来源认证、数据加密、数据完整性和抗重放功能来保证通信双方Internet上传输数据的安全性。 IPSec 架构IPSec VPN体系结构主要由AH(Authentication Header)、ESP(Encapsulating Security Payload)和IKE(Internet Key Exchange)协议套件组成。通过AH和ESP这两个安全协议来实现IP数据报文的安全传送。 AH协议:主要提供的功能有数据源验证、数据完整性校验和防报文重放功能。然而,AH并不加密所保护的数据报。ESP协议:提供AH协议的所有功能外(但其数据完整性校验不包括IP头),还可提供对IP报文的加密功能。IKE协议:用于自动协商AH和ESP所使用的密码算法,建立和维护安全联盟SA等服务。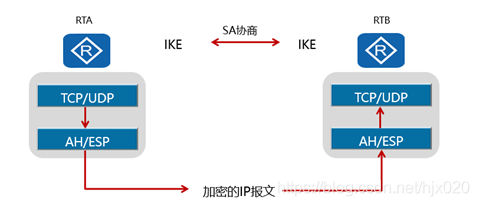 项目背景
项目背景
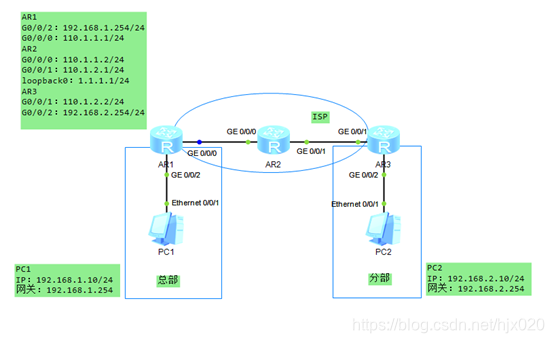
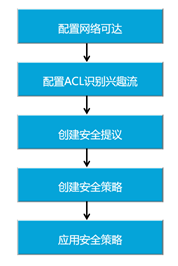
企业对网络安全性的需求日益提升,而传统的TCP/IP协议缺乏有效的安全认证和保密机制。IPSec(Internet Protocol Security)作为一种开放标准的安全框架结构,可以用来保证IP数据报文在网络上传输的机密性、完整性和防重放。 如下图所示,AR1为企业总部网关,AR3为企业分部网关,总部与分部通过公网建立通信。总部子网为192.168.1.0/24,分部子网为192.168.2.0/24,AR2模拟ISP,用loopbacke口模拟公网IP。 企业希望对总部子网与分部子网之间相互访问的流量进行安全保护。总部与分部通过公网建立通信,可以在总部网关与分部网关之间建立一个IPSec隧道来实施安全保护。 本实验用ACL方式建立IPSec隧道,分别演示手工方式和IKE动态协商方式。 手工方式:SA所需的全部信息都必须手工配置。IKE动态协商方式:由IKE协议完成密钥的自动协商,实现动态协商来创建和维护SA。
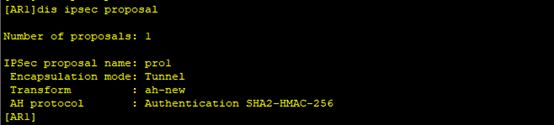
1. 在AR2上配置设备名和接口的IP地址,模拟ISP网络。 system-view [Huawei] sysname AR2 [AR2] interface GigabitEthernet0/0/0 [AR2-GigabitEthernet0/0/0] ip address 110.1.1.2 255.255.255.0 [AR2-GigabitEthernet0/0/0] quit [AR2]interface GigabitEthernet0/0/1 [AR2-GigabitEthernet0/0/1] ip address 110.1.2.1 255.255.255.0 [AR2-GigabitEthernet0/0/1] quit [AR2]interface LoopBack0 [AR2-LoopBack0] ip address 1.1.1.1 255.255.255.0 [AR2-LoopBack0] quit2. 分别在AR1和AR3上配置设备名、接口的IP地址和默认路由,保证两路由器之间可以互通。 #在AR1上配置设备名和接口的IP地址 system-view [Huawei] sysname AR1 [AR1] interface GigabitEthernet0/0/0 [AR1-GigabitEthernet0/0/0] ip address 110.1.1.1 255.255.255.0 [AR1-GigabitEthernet0/0/0] quit [AR1]interface GigabitEthernet0/0/2 [AR1-GigabitEthernet0/0/2] ip address 192.168.1.254 255.255.255.0 [AR1-GigabitEthernet0/0/2] quit#在AR1上配置默认路由 [AR1] ip route-static 0.0.0.0 0.0.0.0 110.1.1.2#在AR3上配置设备名和接口的IP地址 system-view [Huawei] sysname AR3 [AR3] interface GigabitEthernet0/0/1 [AR3-GigabitEthernet0/0/1] ip address 110.1.2.2 255.255.255.0 [AR3-GigabitEthernet0/0/1] quit [AR3]interface GigabitEthernet0/0/2 [AR3-GigabitEthernet0/0/2] ip address 192.168.1.254 255.255.255.0 [AR3-GigabitEthernet0/0/2] quit#在AR3上配置默认路由 [AR3] ip route-static 0.0.0.0 0.0.0.0 110.1.2.13. 分别在AR1和AR3上配置ACL,以定义各自需要保护的IPSec数据流。 #在AR1上配置ACL,定义由子网192.168.1.0/24去子网192.168.2.0/24的数据流。 [AR1] acl number 3000 [AR1-acl-adv-3000] rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 [AR1-acl-adv-3000] quit#在AR3上配置ACL,定义由子网192.168.2.0/24去子网192.168.1.0/24的数据流。 [AR3] acl number 3000 [AR3-acl-adv-3000] rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 [AR3-acl-adv-3000] quit4. 分别在AR1和AR3上配置IPSec安全提议,定义IPSec的保护方法。 #在AR1上配置IPSec安全提议。 [AR1] ipsec proposal pro1 [AR1-ipsec-proposal- pro1] transform ah [AR1-ipsec-proposal- pro1] ah authentication-algorithm sha2-256 [AR1-ipsec-proposal- pro1] quit#在AR3上配置IPSec安全提议。 [AR3] ipsec proposal pro1 [AR3-ipsec-proposal- pro1] transform ah [AR3-ipsec-proposal- pro1] ah authentication-algorithm sha2-256 [AR3-ipsec-proposal- pro1] quit此时分别在AR1和AR3上执行display ipsec proposal会显示所配置的信息 #在AR3上配置手工方式安全策略。 [AR3] ipsec policy ipsec 1 manual [AR3-ipsec-policy-manual-ipsec-1] security acl 3000 [AR3-ipsec-policy-manual-ipsec-1] proposal pro1 [AR3-ipsec-policy-manual-ipsec-1] tunnel local 110.1.2.2 [AR3-ipsec-policy-manual-ipsec-1] tunnel remote 110.1.1.1 [AR3-ipsec-policy-manual-ipsec-1] sa spi inbound ah 54321 [AR3-ipsec-policy-manual-ipsec-1] sa string-key inbound ah cipher huawei [AR3-ipsec-policy-manual-ipsec-1] sa spi outbound ah 12345 [AR3-ipsec-policy-manual-ipsec-1] sa string-key outbound ah cipher huawei [AR3-ipsec-policy-manual-ipsec-1] quit此时分别在AR1和AR3上执行display ipsec sa会显示所配置的信息。 #在AR3的接口上引用安全策略组。 [AR3] interface gigabitethernet 0/0/1 [AR3-GigabitEthernet0/0/1] ipsec policy ipsec [AR3-GigabitEthernet0/0/1] quit在总部PC1 ping 分部PC2
#在AR3上配置NAT。 [AR3] acl number 3001 [AR3-acl-adv-3001] rule deny ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 [AR3-acl-adv-3001] rule permit ip [AR3-acl-adv-3001] quit [AR3] interface GigabitEthernet0/0/0 [AR3-acl-adv-3001] nat outbound 3001 [AR3-acl-adv-3001] quit在PC1 ping 1.1.1.1 #在AR3上修改IPSec安全提议配置 [AR3] ipsec proposal pro1 [AR3-ipsec-proposal- pro1] transform esp [AR3-ipsec-proposal- pro1] esp authentication-algorithm sha2-256 [AR3-ipsec-proposal- pro1] esp encryption-algorithm 3des [AR3-ipsec-proposal- pro1] quit此时分别在AR1和AR3上执行display ipsec proposal会显示所配置的信息。 #在AR3上修改IPSec安全策略配置 [AR3] ipsec policy ipsec 1 manual [AR3-ipsec-policy-manual-ipsec-1] undo sa spi inbound ah [AR3-ipsec-policy-manual-ipsec-1] sa spi inbound esp 54321 [AR3-ipsec-policy-manual-ipsec-1] undo sa string-key inbound ah [AR3-ipsec-policy-manual-ipsec-1] sa string-key inbound esp cipher huawei [AR3-ipsec-policy-manual-ipsec-1] undo sa spi outbound ah [AR3-ipsec-policy-manual-ipsec-1] sa spi outbound esp 12345 [AR3-ipsec-policy-manual-ipsec-1] undo sa string-key outbound ah [AR3-ipsec-policy-manual-ipsec-1] sa string-key outbound esp cipher hauwei [AR3-ipsec-policy-manual-ipsec-1] quit此时分别在AR1和AR3上执行display ipsec sa会显示所配置的信息。 1. 沿用上一个实验的拓扑,在原有配置上修改成IKE协商方式建立IPSec。(其中接口ip地址、默认路由、NAT和IPSec安全提议配置都沿用上个实验的配置) 2. 分别在AR1和AR3上配置IKE对等体 #在AR1上配置IKE安全提议。 [AR1] ike proposal 10 [AR1-ike-proposal-10] encryption-algorithm des-cbc [AR1-ike-proposal-10] authentication-algorithm sha1 [AR1-ike-proposal-10] quit#在AR1上配置IKE对等体,并根据默认配置,配置预共享密钥和对端ID。 [AR1] ike peer peer v1 [AR1-ike-peer- peer] ike-proposal 10 [AR1-ike-peer- peer] pre-shared-key cipher huawei [AR1-ike-peer- peer] remote-address 110.1.2.2 [AR1-ike-peer- peer] quit#在AR3上配置IKE安全提议。 [AR3] ike proposal 10 [AR3-ike-proposal-10] encryption-algorithm des-cbc [AR3-ike-proposal-10] authentication-algorithm sha1 [AR3-ike-proposal-10] quit#在AR3上配置IKE对等体,并根据默认配置,配置预共享密钥和对端ID。 [AR3] ike peer peer v1 [AR3-ike-peer- peer] ike-proposal 10 [AR3-ike-peer- peer] pre-shared-key cipher huawei [AR3-ike-peer- peer] remote-address 110.1.1.1 [AR3-ike-peer- peer] quit3. 分别在AR1和AR3上创建安全策略 #在AR1上配置IKE动态协商方式安全策略。 [AR1] ipsec policy ipsec1 1 isakmp [AR1-ipsec-policy-isakmp- ipsec1-1] ike-peer peer [AR1-ipsec-policy-isakmp- ipsec1-1] proposal pro1 [AR1-ipsec-policy-isakmp- ipsec1-1] security acl 3000 [AR1-ipsec-policy-isakmp- ipsec1-1] quit#在AR3上配置IKE动态协商方式安全策略。 [AR3] ipsec policy ipsec1 1 isakmp [AR3-ipsec-policy-isakmp- ipsec1-1] ike-peer peer [AR3-ipsec-policy-isakmp- ipsec1-1] proposal pro1 [AR3-ipsec-policy-isakmp- ipsec1-1] security acl 3000 [AR3-ipsec-policy-isakmp- ipsec1-1] quit此时分别在AR1和AR3上执行display ipsec policy name ipsec1会显示所配置的信息。 #在AR3的接口上修改引用安全策略组。 [AR3] interface gigabitethernet 0/0/1 [AR3-GigabitEthernet0/0/1] undo ipsec policy ipsec [AR3-GigabitEthernet0/0/1] ipsec policy ipsec1 [AR3-GigabitEthernet0/0/1] quit在总部的PC1上ping分部的PC2和ISP。 配置文件 AR1 # sysname AR1 # acl number 3000 rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 acl number 3001 rule 5 deny ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 rule 10 permit ip # ipsec proposal pro1 esp authentication-algorithm sha2-256 esp encryption-algorithm 3des # ipsec policy ipsec 1 manual security acl 3000 proposal pro1 tunnel local 110.1.1.1 tunnel remote 110.1.2.2 sa spi inbound esp 12345 sa string-key inbound esp cipher huawei sa spi outbound esp 54321 sa string-key outbound esp cipher hauwei # ike proposal 10 # ike peer peer v1 pre-shared-key cipher huawei ike-proposal 10 remote-address 110.1.2.2 # ipsec policy ipsec1 1 isakmp security acl 3000 ike-peer peer proposal pro1 # interface GigabitEthernet0/0/0 ip address 110.1.1.1 255.255.255.0 ipsec policy ipsec1 nat outbound 3001 # interface GigabitEthernet0/0/2 ip address 192.168.1.254 255.255.255.0 # ip route-static 0.0.0.0 0.0.0.0 110.1.1.2 AR3 # sysname AR3 # acl number 3000 rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 acl number 3001 rule 5 deny ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 rule 10 permit ip # ipsec proposal pro1 esp authentication-algorithm sha2-256 esp encryption-algorithm 3des # ipsec policy ipsec 1 manual security acl 3000 proposal pro1 tunnel local 110.1.2.2 tunnel remote 110.1.1.1 sa spi inbound esp 54321 sa string-key inbound esp cipher huawei sa spi outbound esp 12345 sa string-key outbound esp cipher huawei # ike proposal 10 # ike peer peer v1 pre-shared-key cipher hauwei ike-proposal 10 remote-address 110.1.1.1 # ipsec policy ipsec1 1 isakmp security acl 3000 ike-peer peer proposal pro1 # interface GigabitEthernet0/0/1 ip address 110.1.2.2 255.255.255.0 ipsec policy ipsec1 nat outbound 3001 # interface GigabitEthernet0/0/2 ip address 192.168.2.254 255.255.255.0 # ip route-static 0.0.0.0 0.0.0.0 110.1.2.1作者:蔡宗唐 排版:梁汉荣、十六 审核:正月十六 点击下方“正月十六工作室”查看更多学习资源 正月十六工作室 |
【本文地址】
今日新闻 |
推荐新闻 |
 5. 配置安全策略,并引用ACL和IPSec安全提议,确定对何种数据流采取何种保护方法。 #在AR1上配置手工方式安全策略。
5. 配置安全策略,并引用ACL和IPSec安全提议,确定对何种数据流采取何种保护方法。 #在AR1上配置手工方式安全策略。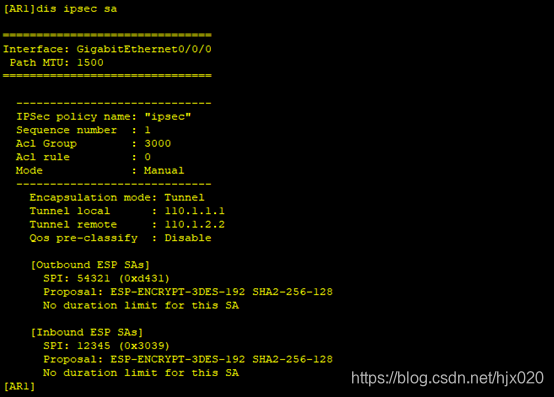
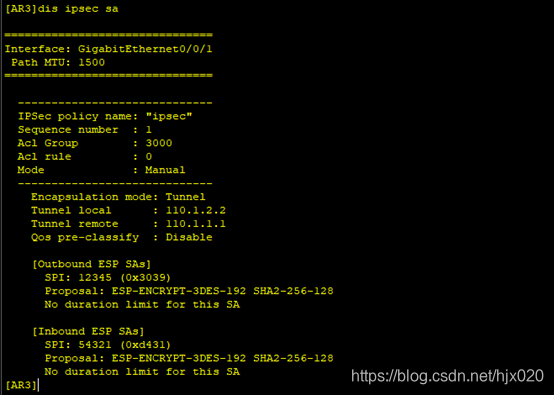 6. 分别在AR1和AR3的接口上应用安全策略组,使接口具有IPSec的保护功能。 #在AR1的接口上引用安全策略组。
6. 分别在AR1和AR3的接口上应用安全策略组,使接口具有IPSec的保护功能。 #在AR1的接口上引用安全策略组。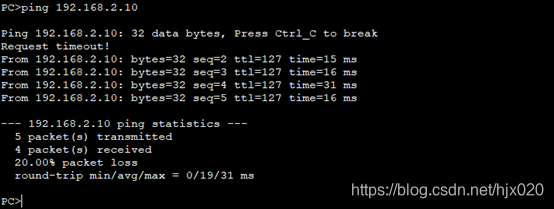 抓包分析
抓包分析 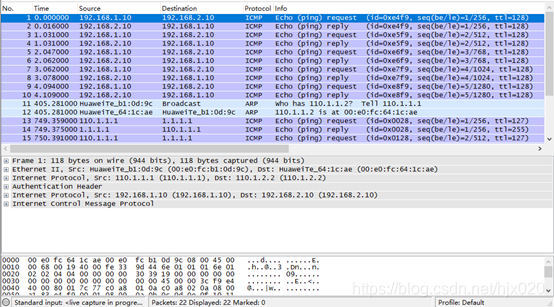 7. 分别在AR1和AR3配置NAT,使得内网PC能够ping通ISP。 #在AR1上配置NAT。
7. 分别在AR1和AR3配置NAT,使得内网PC能够ping通ISP。 #在AR1上配置NAT。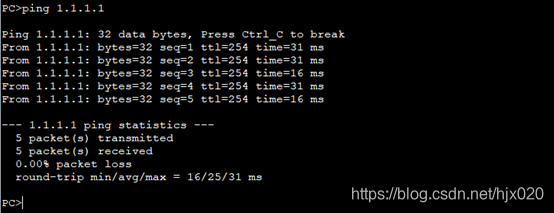 抓包分析
抓包分析 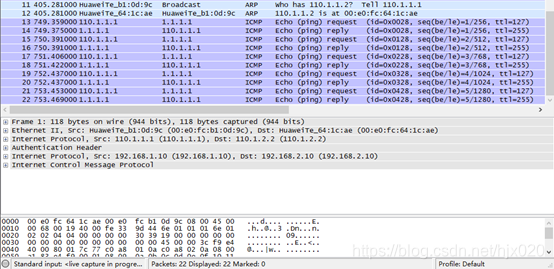 8.分别在AR1和AR3上修改IPSec安全提议中的安全协议ah为esp #在AR1上修改IPSec安全提议配置
8.分别在AR1和AR3上修改IPSec安全提议中的安全协议ah为esp #在AR1上修改IPSec安全提议配置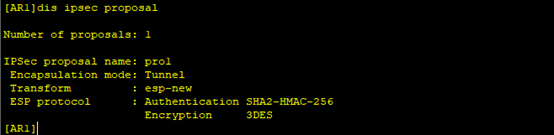
 9. 分别在AR1和AR3上修改IPSec安全策略配置。 #在AR1上修改IPSec安全策略配置
9. 分别在AR1和AR3上修改IPSec安全策略配置。 #在AR1上修改IPSec安全策略配置
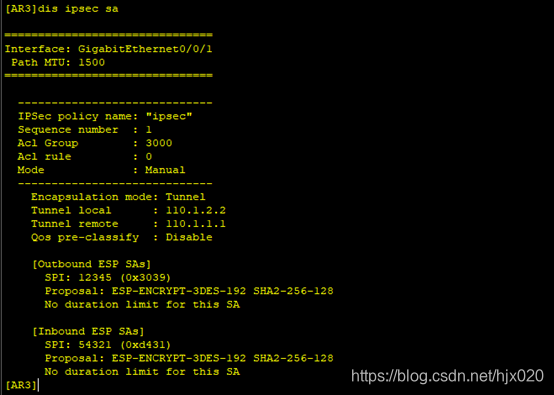 抓包分析
抓包分析 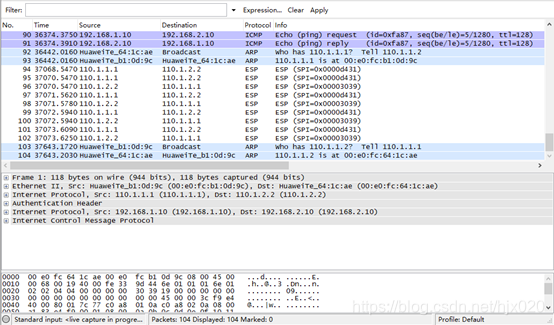 配置文件
配置文件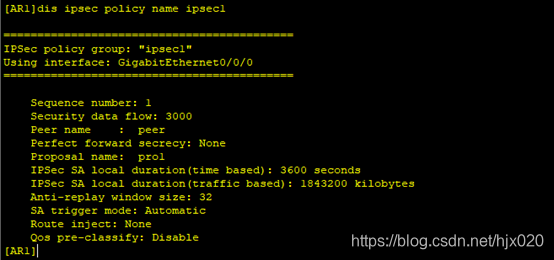
 4. 分别在AR1和AR3的接口上应用各自的安全策略组,使接口具有IPSec的保护功能 #在AR1的接口上修改引用的安全策略组。
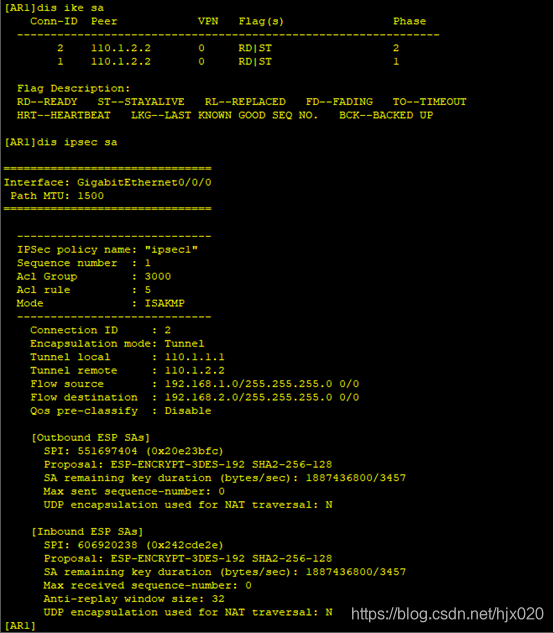
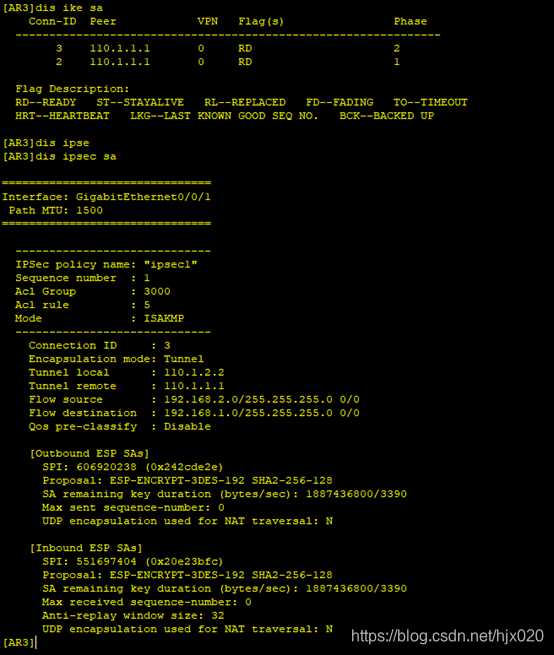
4. 分别在AR1和AR3的接口上应用各自的安全策略组,使接口具有IPSec的保护功能 #在AR1的接口上修改引用的安全策略组。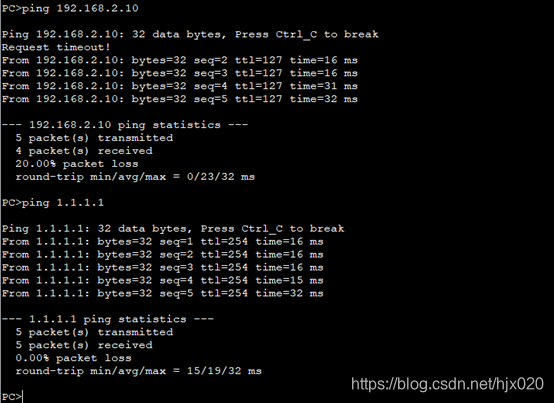 5. 分别在AR1和AR3上执行display ike sa和display ipsec sa,结果如下
5. 分别在AR1和AR3上执行display ike sa和display ipsec sa,结果如下